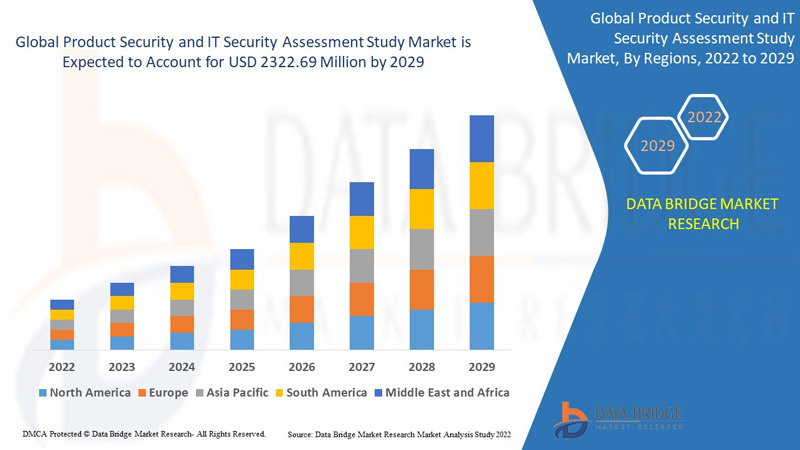
Global Product Security And It Security Assessment Study Market
Market Size in USD Billion
CAGR :
% 
 USD
1,221.01 Billion
USD
2,322.69 Billion
2021
2029
USD
1,221.01 Billion
USD
2,322.69 Billion
2021
2029
| 2022 –2029 | |
| USD 1,221.01 Billion | |
| USD 2,322.69 Billion | |
|
|
|
Product Security and IT Security Assessment Study Market Analysis and Size
Cybercrime is the fastest-growing crime in all over the globe. This has made cybersecurity an essential need of the hour in government bodies, businesses, and the financial sector. Its deployment has been driven remotely by everything that uses data, thus considerably contributing to product security and IT security assessment study adoption. Several industries are adopting advanced cybersecurity solutions such as network assessment and IT Security certifications to enhance protection against cybercrime. The increasing need for solutions ranging from next-generation firewalls, DNS filtering, antivirus software, unified threat management system, threat intelligence and malware protection will boost the demand for cyber security and impel the market growth.
Data Bridge Market Research analyses that the product security and IT security assessment study market was valued at USD 1221.01 million in 2021 and is expected to reach the value of USD 2322.69 million by 2029, at a CAGR of 8.37% during the forecast period. In addition to the market insights such as market value, growth rate, market segments, geographical coverage, market players, and market scenario, the market report curated by the Data Bridge Market Research team includes in-depth expert analysis, import/export analysis, pricing analysis, production consumption analysis, and pestle analysis.
Product Security and IT Security Assessment Study Market Scope and Segmentation
|
Report Metric |
Details |
|
Forecast Period |
2022 to 2029 |
|
Base Year |
2021 |
|
Historic Years |
2020 (Customizable to 2014 - 2019) |
|
Quantitative Units |
Revenue in USD Million, Volumes in UnITs, Pricing in USD |
|
Segments Covered |
By Security Type (Endpoint Security, Network Security, Application Security, Cloud Security, and Others), Assessment Type (Endpoint Security, Network Security, Application Security, Cloud Security, and Others), Deployment (On-Premise, Hosted), Organization Size (Small and Medium-Sized Enterprises, Large Enterprises), End User (BFSI, IT and Telecommunications, Government and Defence, Energy and Utilities, Manufacturing, Healthcare, Retail) |
|
Countries Covered |
U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, Israel, Egypt, South Africa, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America |
|
Market Players Covered |
IBM (U.S.), Microsoft (U.S.), Cisco System Inc, (U.S.), SolarWinds Worldwide, LLC. (U.S.), Symantec Corporation (U.S.), Avast Software s.r.o, (Czechia), Comodo Security Solutions, Inc. (U.S.), Tenable, Inc (U.S.), Armor Defense Inc. (U.S.), Fujitsu (Japan), Fortinet, Inc. (U.S.), Zoho Corporation Pvt. Ltd. (India), Trend Micro Incorporated (U.S.), Hitachi (Japan), Juniper Networks, Inc. (U.S.), McAfee, LLC.(U.S.), NEC Corporation (Japan) |
|
Market Opportunities |
|
Market Definition
Security assessments are periodic exercises that majorly evaluate an organization's level of security readiness. These evaluations generally involve checking for weaknesses in the operational procedures and company's IT systems and making recommendations for essential actions to decrease the likelihood of future security-related attacks.
Global Product Security and IT Security Assessment Study Market
Drivers
- Increasing usage of product security and IT security assessment study in Banking, Financial Services and Insurance (BFSI)
Banking, Financial Services and Insurance (BFSI) is analyzed to be the hold highest market share followed by the retail sector in all over industries. The steady shift of organizing cloud models for data storage is surely contributing to banks' growing adoption of cloud models. The cloud storage carried additional security and safety concerns due to which the banks trust on the hybrid model for data management. Whereas the hybrid model is measured to be safe because the banks are facing many threats and cyber-attacks by the growing use of one-time-password and fingerprint-based login system,
- Growing threats and cyber-attacks
The growing threats and cyber-attacks are impacting the adoption rate of these solutions. According to cybint, a cyber education firm, nearly 60% of companies have experienced cyber-attacks such as social engineering attacks, DDoS attacks and phishing. With the increasing number of cyber-attacks that several firms are experiencing will create extensive need of product security and IT assessment. This factor is set to escalate the growth rate of the market.
Opportunities
- Surging trend of bring your own device (BYOD)
The trend of bring your own device (BYOD) is certainly increasing as the growing encouragement from the medium and small scale enterprises to use their own devices to access the data. Bring your own device (BYOD) market is set to reach approximately $367 billion by 2022, up from a mere $30 billion in 2014. Therefore with the increasing adoption of this trend the susceptibility of facing cyber threats is high, thus considerably impacting the high adoption of the product security and IT assessment, and are expected to create lucrative opportunities for the market growth rate.
- Increasing shift toward digitization
With a robust shift toward the digital era, unaddressed susceptibilities in end-user industries are also growing parallel. The rise in ransomware is a prominent factor which is creating a need for product security and IT assessment study. According to ransomware survey by Fortinet, in 2021 around 94% of those surveyed specified that they are concerned about threat of a ransomware attack, with 76% being extremely concerned. Of those, 85% more worry about ransomware attack than any other cyber threat. Therefore, there creates a rising need for risk product security and IT assessment that will help the market for further expansion in upcoming.
Restraints
- Lack of awareness about the threats
Many employees and firms are unaware of the cyber threats. 43% of employees believe clicking a doubtful email or link attachment can pose a security threat. Therefore, the attacks are considerably increasing thus hampering the market growth rate. The increasing demand for advanced security systems owing to the IIoT threats, block chain revolution, and AI wave are some challenges which are faced by the vendors in the cyber security market. Moreover, ransomware attacks are increasing rapidly, which is also becoming a foremost challenge to the cybersecurity ventures.
This product security and IT security assessment study market report provides details of new recent developments, trade regulations, import-export analysis, production analysis, value chain optimization, market share, impact of domestic and localized market players, analyses opportunities in terms of emerging revenue pockets, changes in market regulations, strategic market growth analysis, market size, category market growths, application niches and dominance, product approvals, product launches, geographic expansions, technological innovations in the market. To gain more info on the product security and IT security assessment study market contact Data Bridge Market Research for an Analyst Brief, our team will help you take an informed market decision to achieve market growth.
Recent Development
- In September 2019, HP has acquired Bromium, a start-up that offes security from cyber-attacks such as browser-based attacks, infected emails, compromised downloads, and others by shielding the network endpoints.
Global Product Security and IT Security Assessment Study Market Scope
The product security and IT security assessment study market is segmented on the basis of security type, assessment type, deployment, organization size and end user. The growth amongst these segments will help you analyze meagre growth segments in the industries and provide the users with a valuable market overview and market insights to help them make strategic decisions for identifying core market applications.
Security Type
- Endpoint Security
- Network Security
- Application Security
- Cloud Security
- Others
Assessment Type
- Endpoint Security
- Network Security
- Application Security
- Cloud Security
- Others
Deployment
- On-Premise
- Hosted
Organization Size
- Small and Medium-Sized Enterprises
- Large Enterprises
End User
- BFSI
- IT and Telecommunications
- Government and Defence, Energy and Utilities
- Manufacturing
- Healthcare
- Retail
Product Security and IT Security Assessment Study Market Regional Analysis/Insights
The product security and IT security assessment study market is analyzed and market size insights and trends are provided by country, security type, assessment type, deployment, organization size and end user as referenced above.
The countries covered in the product security and IT security assessment study market report are U.S., Canada and Mexico in North America, Germany, France, U.K., Netherlands, Switzerland, Belgium, Russia, Italy, Spain, Turkey, Rest of Europe in Europe, China, Japan, India, South Korea, Singapore, Malaysia, Australia, Thailand, Indonesia, Philippines, Rest of Asia-Pacific (APAC) in the Asia-Pacific (APAC), Saudi Arabia, U.A.E, Israel, Egypt, South Africa, Rest of Middle East and Africa (MEA) as a part of Middle East and Africa (MEA), Brazil, Argentina and Rest of South America as part of South America.
North America dominates the product security and IT security assessment study market. This is mainly due to the high adoption of the low-cost sensitivity and advanced technologies in this region for product security & IT security assessment in majority of the firms.
Asia-Pacific will continue to project the highest compound annual growth rate during the forecast period of 2022-2029 due to the growing requirement for deploying the product security and IT security assessment in this region.
The country section of the report also provides individual market impacting factors and changes in market regulation that impact the current and future trends of the market. Data points like down-stream and upstream value chain analysis, technical trends and porter's five forces analysis, case studies are some of the pointers used to forecast the market scenario for individual countries. Also, the presence and availability of Global brands and their challenges faced due to large or scarce competition from local and domestic brands, impact of domestic tariffs and trade routes are considered while providing forecast analysis of the country data.
Competitive Landscape and Product Security and IT Security Assessment Study Market Share Analysis
The product security and IT security assessment study market competitive landscape provides details by competitor. Details included are company overview, company financials, revenue generated, market potential, investment in research and development, new market initiatives, Global presence, production sites and facilities, production capacities, company strengths and weaknesses, product launch, product width and breadth, application dominance. The above data points provided are only related to the companies' focus related to product security and IT security assessment study market.
Some of the major players operating in the product security and IT security assessment study market are:
- IBM (U.S.)
- Microsoft (U.S.)
- Cisco System Inc, (U.S.)
- SolarWinds Worldwide, LLC. (U.S.)
- Symantec Corporation (U.S.)
- Avast Software s.r.o, (Czechia)
- Comodo Security Solutions, Inc. (U.S.)
- Tenable, Inc (U.S.)
- Armor Defense Inc. (U.S.)
- Fujitsu (Japan)
- Fortinet, Inc. (U.S.)
- Zoho Corporation Pvt. Ltd. (India)
- Trend Micro Incorporated (U.S.)
- Hitachi (Japan)
- Juniper Networks, Inc. (U.S.)
- McAfee, LLC.(U.S.)
- NEC Corporation (Japan)
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Table of Content
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATION
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 KEY TAKEAWAYS
2.2 ARRIVING AT THE GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET
2.2.1 VENDOR POSITIONING GRID
2.2.2 TECHNOLOGY LIFE LINE CURVE
2.2.3 MARKET GUIDE
2.2.4 COMPANY POSITIONING GRID
2.2.5 MULTIVARIATE MODELLING
2.2.6 STANDARDS OF MEASUREMENT
2.2.7 TOP TO BOTTOM ANALYSIS
2.2.8 VENDOR SHARE ANALYSIS
2.2.9 DATA POINTS FROM KEY PRIMARY INTERVIEWS
2.2.10 DATA POINTS FROM KEY SECONDARY DATABASES
2.3 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET: RESEARCH SNAPSHOT
2.4 ASSUMPTIONS
3 MARKET OVERVIEW
3.1 DRIVERS
3.2 RESTRAINTS
3.3 OPPORTUNITIES
3.4 CHALLENGES
4 EXECUTIVE SUMMARY
5 PREMIUM INSIGHTS
5.1 REGULATORY IMPLICATIONS AND INDUSTRY STANDARDS
5.2 TECHNOLOGICAL TRENDS
5.3 PORTERS FIVE FORCES MODEL
6 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY OFFERING
6.1 OVERVIEW
6.2 SOLUTION
6.3 SERVICES
6.3.1 PROFESSIONAL SERVICES
6.3.2 MANAGED SERVICES
7 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY SECURITY TYPE
7.1 OVERVIEW
7.2 ENDPOINT SECURITY
7.3 NETWORK SECURITY
7.4 APPLICATION SECURITY
7.4.1 STATIC APPLICATION SECURITY TESTING (SAST)
7.4.2 DYNAMIC APPLICATION SECURITY TESTING (DAST)
7.4.3 INTERACTIVE APPLICATION SECURITY TESTING (IAST)
7.4.4 RUN-TIME APPLICATION SELF PROTECTION (RASP)
7.5 DEVICE SECURITY
7.6 DATA SECURITY
7.7 CLOUD SECURITY
7.7.1 CLOUD EMAIL SECURITY
7.7.2 CLOUD WEB SECURITY
7.7.3 IDENTITY AND ACCESS MANAGEMENT
7.7.4 IDENTITY AS A SERVICE (IDAAS) AND USER AUTHENTICATION
7.7.5 REMOTE VULNERABILITY ASSESSMENT
7.7.6 SECURITY INFORMATION AND EVENT MANAGEMENT (SIEM)
7.7.7 APPLICATION SECURITY TESTING
7.7.8 OTHER TYPES
7.8 OTHERS
8 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY ASSESSMENT TYPE
8.1 OVERVIEW
8.2 VULNERABILITY ASSESSMENT
8.3 RISK ASSESSMENT
8.4 THREAT ASSESSMENT
8.5 PENETRATION TESTING SERVICE
8.6 SECURITY PROGRAM ASSESSMENT
8.7 OTHERS
9 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY DEPLOYMENT MODE
9.1 OVERVIEW
9.2 ON-PREMISE
9.3 CLOUD
10 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY ORGANIZATION SIZE
10.1 OVERVIEW
10.2 LARGE ENTERPRISE
10.3 SMALL & MEDIUM ENTERPRISE (SMES)
11 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY VERTICAL
11.1 OVERVIEW
11.2 BFSI
11.2.1 SOLUTION
11.2.2 SERVICES
11.3 IT & TELECOM
11.3.1 SOLUTION
11.3.2 SERVICES
11.4 GOVERNMENT & DEFENSE
11.4.1 SOLUTION
11.4.2 SERVICES
11.5 ENERGY & UTILITIES
11.5.1 SOLUTION
11.5.2 SERVICES
11.6 RETAIL & ECOMMERCE
11.6.1 SOLUTION
11.6.2 SERVICES
11.7 MANUFACTURING
11.7.1 SOLUTION
11.7.2 SERVICES
11.8 HEALTHCARE
11.8.1 SOLUTION
11.8.2 SERVICES
11.9 EDUCATION
11.9.1 SOLUTION
11.9.2 SERVICES
11.1 OTHERS
12 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, BY REGION
GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, (ALL SEGMENTATION PROVIDED ABOVE IS REPRESENTED IN THIS CHAPTER BY COUNTRY)
12.1 NORTH AMERICA
12.1.1 U.S.
12.1.2 CANADA
12.1.3 MEXICO
12.2 EUROPE
12.2.1 GERMANY
12.2.2 FRANCE
12.2.3 U.K.
12.2.4 ITALY
12.2.5 SPAIN
12.2.6 RUSSIA
12.2.7 TURKEY
12.2.8 BELGIUM
12.2.9 NETHERLANDS
12.2.10 SWITZERLAND
12.2.11 REST OF EUROPE
12.3 ASIA PACIFIC
12.3.1 JAPAN
12.3.2 CHINA
12.3.3 SOUTH KOREA
12.3.4 INDIA
12.3.5 AUSTRALIA
12.3.6 SINGAPORE
12.3.7 THAILAND
12.3.8 MALAYSIA
12.3.9 INDONESIA
12.3.10 PHILIPPINES
12.3.11 REST OF ASIA PACIFIC
12.4 SOUTH AMERICA
12.4.1 BRAZIL
12.4.2 ARGENTINA
12.4.3 REST OF SOUTH AMERICA
12.5 MIDDLE EAST AND AFRICA
12.5.1 SOUTH AFRICA
12.5.2 EGYPT
12.5.3 SAUDI ARABIA
12.5.4 U.A.E
12.5.5 ISRAEL
12.5.6 REST OF MIDDLE EAST AND AFRICA
13 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, COMPANY LANDSCAPE
13.1 COMPANY SHARE ANALYSIS: GLOBAL
13.2 COMPANY SHARE ANALYSIS: NORTH AMERICA
13.3 COMPANY SHARE ANALYSIS: EUROPE
13.4 COMPANY SHARE ANALYSIS: ASIA-PACIFIC
13.5 MERGERS & ACQUISITIONS
13.6 NEW PRODUCT DEVELOPMENT AND APPROVALS
13.7 EXPANSIONS
13.8 REGULATORY CHANGES
13.9 PARTNERSHIP AND OTHER STRATEGIC DEVELOPMENTS
14 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, SWOT AND DBMR ANALYSIS
15 GLOBAL PRODUCT SECURITY AND IT SECURITY ASSESSMENT STUDY MARKET, COMPANY PROFILE
15.1 IBM CORPORATION
15.1.1 COMPANY SNAPSHOT
15.1.2 REVENUE ANALYSIS
15.1.3 GEOGRAPHIC PRESENCE
15.1.4 PRODUCT PORTFOLIO
15.1.5 RECENT DEVELOPMENTS
15.2 FIREEYE, INC.
15.2.1 COMPANY SNAPSHOT
15.2.2 REVENUE ANALYSIS
15.2.3 GEOGRAPHIC PRESENCE
15.2.4 PRODUCT PORTFOLIO
15.2.5 RECENT DEVELOPMENTS
15.3 CISCO SYSTEMS
15.3.1 COMPANY SNAPSHOT
15.3.2 REVENUE ANALYSIS
15.3.3 GEOGRAPHIC PRESENCE
15.3.4 PRODUCT PORTFOLIO
15.3.5 RECENT DEVELOPMENTS
15.4 SOLARWINDS WORLDWIDE
15.4.1 COMPANY SNAPSHOT
15.4.2 REVENUE ANALYSIS
15.4.3 GEOGRAPHIC PRESENCE
15.4.4 PRODUCT PORTFOLIO
15.4.5 RECENT DEVELOPMENTS
15.5 MICRO INCORPORATED.
15.5.1 COMPANY SNAPSHOT
15.5.2 REVENUE ANALYSIS
15.5.3 GEOGRAPHIC PRESENCE
15.5.4 PRODUCT PORTFOLIO
15.5.5 RECENT DEVELOPMENTS
15.6 SYMANTEC CORPORATION
15.6.1 COMPANY SNAPSHOT
15.6.2 REVENUE ANALYSIS
15.6.3 GEOGRAPHIC PRESENCE
15.6.4 PRODUCT PORTFOLIO
15.6.5 RECENT DEVELOPMENTS
15.7 AVAST SOFTWARE S.R.O
15.7.1 COMPANY SNAPSHOT
15.7.2 REVENUE ANALYSIS
15.7.3 GEOGRAPHIC PRESENCE
15.7.4 PRODUCT PORTFOLIO
15.7.5 RECENT DEVELOPMENTS
15.8 COMODO SECURITY SOLUTIONS, INC.
15.8.1 COMPANY SNAPSHOT
15.8.2 REVENUE ANALYSIS
15.8.3 GEOGRAPHIC PRESENCE
15.8.4 PRODUCT PORTFOLIO
15.8.5 RECENT DEVELOPMENTS
15.9 TENABLE, INC.
15.9.1 COMPANY SNAPSHOT
15.9.2 REVENUE ANALYSIS
15.9.3 GEOGRAPHIC PRESENCE
15.9.4 PRODUCT PORTFOLIO
15.9.5 RECENT DEVELOPMENTS
15.1 ARMOR DEFENSE INC.
15.10.1 COMPANY SNAPSHOT
15.10.2 REVENUE ANALYSIS
15.10.3 GEOGRAPHIC PRESENCE
15.10.4 PRODUCT PORTFOLIO
15.10.5 RECENT DEVELOPMENTS
15.11 TORRID NETWORKS
15.11.1 COMPANY SNAPSHOT
15.11.2 REVENUE ANALYSIS
15.11.3 GEOGRAPHIC PRESENCE
15.11.4 PRODUCT PORTFOLIO
15.11.5 RECENT DEVELOPMENTS
15.12 FORTINET
15.12.1 COMPANY SNAPSHOT
15.12.2 REVENUE ANALYSIS
15.12.3 GEOGRAPHIC PRESENCE
15.12.4 PRODUCT PORTFOLIO
15.12.5 RECENT DEVELOPMENTS
15.13 CA TECHNOLOGIE
15.13.1 COMPANY SNAPSHOT
15.13.2 REVENUE ANALYSIS
15.13.3 GEOGRAPHIC PRESENCE
15.13.4 PRODUCT PORTFOLIO
15.13.5 RECENT DEVELOPMENTS
15.14 HITACH
15.14.1 COMPANY SNAPSHOT
15.14.2 REVENUE ANALYSIS
15.14.3 GEOGRAPHIC PRESENCE
15.14.4 PRODUCT PORTFOLIO
15.14.5 RECENT DEVELOPMENTS
15.15 JUNIPER NETWOR
15.15.1 COMPANY SNAPSHOT
15.15.2 REVENUE ANALYSIS
15.15.3 GEOGRAPHIC PRESENCE
15.15.4 PRODUCT PORTFOLIO
15.15.5 RECENT DEVELOPMENTS
15.16 MCAFEE
15.16.1 COMPANY SNAPSHOT
15.16.2 REVENUE ANALYSIS
15.16.3 GEOGRAPHIC PRESENCE
15.16.4 PRODUCT PORTFOLIO
15.16.5 RECENT DEVELOPMENTS
15.17 MICROSOFT
15.17.1 COMPANY SNAPSHOT
15.17.2 REVENUE ANALYSIS
15.17.3 GEOGRAPHIC PRESENCE
15.17.4 PRODUCT PORTFOLIO
15.17.5 RECENT DEVELOPMENTS
15.18 NEC
15.18.1 COMPANY SNAPSHOT
15.18.2 REVENUE ANALYSIS
15.18.3 GEOGRAPHIC PRESENCE
15.18.4 PRODUCT PORTFOLIO
15.18.5 RECENT DEVELOPMENTS
15.19 ABSOLUTE SOFTWARE CORP
15.19.1 COMPANY SNAPSHOT
15.19.2 REVENUE ANALYSIS
15.19.3 GEOGRAPHIC PRESENCE
15.19.4 PRODUCT PORTFOLIO
15.19.5 RECENT DEVELOPMENTS
15.2 QUALYS INC
15.20.1 COMPANY SNAPSHOT
15.20.2 REVENUE ANALYSIS
15.20.3 GEOGRAPHIC PRESENCE
15.20.4 PRODUCT PORTFOLIO
15.20.5 RECENT DEVELOPMENTS
15.21 OPTIV SECURITY INC
15.21.1 COMPANY SNAPSHOT
15.21.2 REVENUE ANALYSIS
15.21.3 GEOGRAPHIC PRESENCE
15.21.4 PRODUCT PORTFOLIO
15.21.5 RECENT DEVELOPMENTS
15.22 HOLM SECURITY
15.22.1 COMPANY SNAPSHOT
15.22.2 REVENUE ANALYSIS
15.22.3 GEOGRAPHIC PRESENCE
15.22.4 PRODUCT PORTFOLIO
15.22.5 RECENT DEVELOPMENTS
15.23 RAPID7 INC
15.23.1 COMPANY SNAPSHOT
15.23.2 REVENUE ANALYSIS
15.23.3 GEOGRAPHIC PRESENCE
15.23.4 PRODUCT PORTFOLIO
15.23.5 RECENT DEVELOPMENTS
15.24 CHECK POINT SOFTWARE TECHNOLOGIES LTD.
15.24.1 COMPANY SNAPSHOT
15.24.2 REVENUE ANALYSIS
15.24.3 GEOGRAPHIC PRESENCE
15.24.4 PRODUCT PORTFOLIO
15.24.5 RECENT DEVELOPMENTS
15.25 VERACODE
15.25.1 COMPANY SNAPSHOT
15.25.2 REVENUE ANALYSIS
15.25.3 GEOGRAPHIC PRESENCE
15.25.4 PRODUCT PORTFOLIO
15.25.5 RECENT DEVELOPMENTS
*NOTE: THE COMPANIES PROFILED IS NOT EXHAUSTIVE LIST AND IS AS PER OUR PREVIOUS CLIENT REQUIREMENT. WE PROFILE MORE THAN 100 COMPANIES IN OUR STUDIES AND HENCE THE LIST OF COMPANIES CAN BE MODIFIED OR REPLACED ON REQUEST
16 CONCLUSION
17 QUESTIONNAIRE
18 RELATED REPORTS
19 ABOUT DATA BRIDGE MARKET RESEARCH
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.