Global Automated Breach And Attack Simulation Market
Market Size in USD Billion
CAGR :
% 
 USD
1.12 Billion
USD
5.01 Billion
2024
2032
USD
1.12 Billion
USD
5.01 Billion
2024
2032
| 2025 –2032 | |
| USD 1.12 Billion | |
| USD 5.01 Billion | |
|
|
|
|
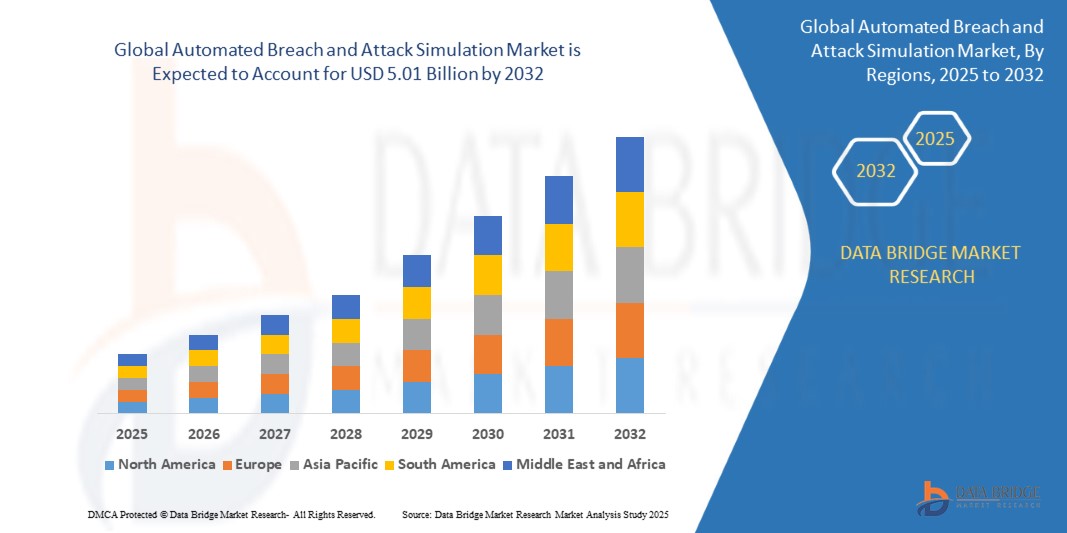
Automated Breach and Attack Simulation Market Size
- The global automated breach and attack simulation (BAS) market was valued at USD 1.12 billion in 2024 and is projected to reach USD 5.01 billion by 2032, growing at a CAGR of 23.86% during the forecast period.
- This growth is fueled by the increasing need for continuous security validation, rising sophistication of cyber threats, and growing demand for automated red teaming and penetration testing across large enterprises and government agencies.
Automated Breach and Attack Simulation Market Analysis
- BAS platforms enable enterprises to simulate real-world cyberattacks on their IT infrastructure in a safe, controlled environment. These platforms test the effectiveness of existing security controls, identify vulnerabilities, and provide prioritized remediation guidance.
- Unlike traditional penetration testing, BAS platforms offer continuous, automated simulations, reducing manual effort and enabling real-time security posture assessments.
- Adoption is increasing among regulated industries like BFSI, healthcare, and government, where regulatory compliance, incident response preparedness, and cyber risk quantification are critical.
- As zero trust architectures and cloud-native ecosystems become more prevalent, BAS is being integrated with XDR, SOAR, SIEM, and vulnerability management platforms to provide a unified, proactive defense approach.
- The rise of AI-driven adversary emulation, MITRE ATT&CK-aligned scenarios, and threat-informed defense strategies is further elevating BAS as a key tool in modern cybersecurity frameworks.
Report Scope and Automated Breach and Attack Simulation Market Segmentation
|
Attributes |
Automated Breach and Attack Simulation Market Key Market Insights |
|
Segments Covered |
|
|
Countries Covered |
North America
Europe
Asia-Pacific
Middle East and Africa
South America
|
|
Key Market Players |
|
|
Market Opportunities |
|
|
Value Added Data Infosets |
In addition to the insights on market scenarios such as market value, growth rate, segmentation, geographical coverage, and major players, the market reports curated by the Data Bridge Market Research also include import export analysis, production capacity overview, production consumption analysis, price trend analysis, climate change scenario, supply chain analysis, value chain analysis, raw material/consumables overview, vendor selection criteria, PESTLE Analysis, Porter Analysis, and regulatory framework. |
Automated Breach and Attack Simulation Market Trends
Security Validation as a Service (SVaaS), Threat-Informed Defense, and SOC Optimization
- Expansion of BAS as a Service (BASaaS/SVaaS): Organizations are increasingly adopting cloud-delivered BAS platforms with preconfigured attack scenarios, reducing the need for internal red teams and speeding time to value.
- Alignment with Threat-Informed Defense Frameworks: BAS solutions are integrating with MITRE ATT&CK, D3FEND, and CIS Controls, helping organizations simulate attacker behavior, map detection gaps, and continuously improve defense posture.
- BAS for SOC Maturity and Blue Team Enablement: Security operations centers are using BAS to test detection rules, validate alerting workflows, and train SOC analysts on real-world attack scenarios without production impact.
- Multi-Vector and Cross-Domain Attack Simulation: Platforms are evolving to simulate multi-stage attacks across cloud, endpoints, identities, and lateral movement paths, offering true enterprise-wide security validation.
- AI and ML in Adversary Emulation: Vendors are leveraging AI to dynamically adjust attack paths, generate novel tactics based on threat intelligence, and improve detection evasion techniques to mimic real adversaries.
Automated Breach and Attack Simulation Market Dynamics
Driver
Demand for Real-Time Security Validation and Threat Exposure Reduction
- Cyberattacks are increasing in complexity, velocity, and evasion techniques, necessitating tools that validate controls continuously rather than relying on periodic testing.
- BAS provides a scalable way to quantify security risk, measure the effectiveness of existing controls, and optimize investments in threat detection technologies.
- Organizations embracing zero trust are leveraging BAS to validate segmentation policies, authentication flows, and lateral movement prevention in dynamic environments.
- With rising cloud adoption, enterprises must continuously test their cloud configurations, IAM policies, and API exposures, making BAS essential for cloud security posture management.
Restraint/Challenge
Integration Complexity and Lack of Skilled BAS Practitioners
- Many enterprises face challenges integrating BAS tools with existing SIEM, XDR, SOAR, and cloud security platforms, often requiring custom connectors or extensive tuning.
- The effectiveness of BAS depends on security operations maturity—organizations lacking well-defined detection and response workflows may struggle to interpret or act on simulation results.
- Smaller organizations often lack the cybersecurity expertise or budget to deploy and maintain a comprehensive BAS platform, making them reliant on managed services or simplified toolsets.
- Privacy and data sovereignty concerns, especially in cross-border simulations, may limit adoption in government or healthcare sectors, where testing in live networks is tightly regulated.
Automated Breach and Attack Simulation Market Scope
The market is segmented by component, deployment mode, application, and end user, reflecting the wide applicability of BAS solutions across sectors and use cases.
- By Component
Platform/Tools lead the market in 2025 due to the high demand for self-service breach simulation and continuous security validation tools. Services (e.g., managed BAS, consulting) are expected to grow at the fastest CAGR, especially among SMEs and highly regulated sectors lacking in-house red teaming capabilities.
- By Deployment Mode
Cloud-based deployment dominates the market due to scalability, ease of integration with cloud-native applications, and reduced setup time. On-premise deployment remains important in government, defense, and financial institutions due to stringent data security and privacy policies.
- By Application
Key applications include configuration management, patch management, threat intelligence validation, and security control performance assessment. Threat intelligence validation is the fastest-growing segment, as organizations seek to align internal defenses with MITRE ATT&CK and external threat data.
- By End User
Includes BFSI, IT & Telecom, Healthcare, Retail & eCommerce, Government, Energy & Utilities, and Others. BFSI leads the market due to increasing cyber insurance requirements, regulatory audits, and attack surface complexity. The government and defense segment is also a major adopter, driven by the need for nation-state threat preparedness and critical infrastructure protection.
Automated Breach and Attack Simulation Market Regional Analysis
- North America dominates the market in 2025 due to early adoption of cyber defense automation, presence of major BAS vendors, and increasing regulatory mandates across banking, healthcare, and critical infrastructure.
- Europe is growing steadily, driven by GDPR compliance, rising nation-state threats, and regional efforts to modernize cyber defense capabilities. The U.K., Germany, and France are key adopters in finance, telecom, and defense.
- Asia-Pacific is the fastest-growing region, led by cybersecurity modernization across Japan, India, China, and Australia. Enterprises are adopting BAS to protect expanding digital ecosystems and critical industries.
- Middle East & Africa (MEA) sees increasing adoption in energy, oil & gas, and government sectors, particularly in UAE and Saudi Arabia, which are investing in cyber threat intelligence platforms and simulation-based training.
- South America, particularly Brazil and Mexico, is deploying BAS in response to rising ransomware attacks and evolving data protection laws. Key sectors include financial services, telecom, and public administration.
United States
The U.S. leads the BAS market due to strong enterprise cybersecurity budgets, cyber defense innovation, and national mandates such as CISA’s security validation programs and NIST cybersecurity frameworks.
United Kingdom
The U.K. has a growing BAS adoption curve among financial institutions, critical infrastructure, and government bodies, driven by NCSC guidelines and increasing focus on adversary emulation.
India
India is emerging as a high-growth BAS market with adoption across IT services, fintech, and telecom sectors. Government-backed cybersecurity initiatives and CERT-In mandates are driving demand for continuous validation tools.
Germany
Germany emphasizes BAS in industrial manufacturing and critical infrastructure, with many companies integrating simulation platforms into security compliance frameworks and industry-specific ISMS protocols.
Brazil
Brazil's adoption of BAS is rising in banking, insurance, and e-government applications, particularly post-LGPD enactment, with emphasis on attack surface reduction and breach readiness validation.
Automated Breach and Attack Simulation Market Share
The Automated Breach and Attack Simulation industry is primarily led by well-established companies, including:
- XM Cyber Ltd. (Israel)
- Cymulate Ltd. (Israel)
- AttackIQ, Inc. (U.S.)
- SafeBreach Inc. (U.S.)
- FireEye, Inc. (Trellix) (U.S.)
- Rapid7 Inc. (U.S.)
- Foreseeti AB (Sweden)
- Qualys, Inc. (U.S.)
- Picus Security Inc. (U.S.)
- Mandiant (acquired by Google Cloud) (U.S.)
- Threatcare (acquired by ReliaQuest) (U.S.)
Latest Developments in Global Automated Breach and Attack Simulation Market
- In April 2025 – XM Cyber introduced its Hybrid Attack Path Mapping Tool, which unifies simulation across on-premise, hybrid, and multi-cloud environments, enabling organizations to visualize full attack chains from initial access to data exfiltration.
- In March 2025 – Cymulate launched Advanced Purple Team Module, allowing cybersecurity teams to collaborate in real time while testing detection, response, and mitigation scenarios through a single simulation interface.
- In February 2025 – AttackIQ released a MITRE ATT&CK Analyzer Suite, enabling automated gap analysis and control validation against industry frameworks for regulated sectors such as finance and healthcare.
- In January 2025 – SafeBreach announced native integration with XDR and SOAR platforms, facilitating automated remediation recommendations based on continuous simulation results and incident data.
- In December 2024 – Mandiant (Google Cloud) unveiled its Adversary Intelligence Module for BAS platforms, combining threat intelligence feeds with dynamic adversary emulation for nation-state threat simulation.
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.