Global Operational Technology Endpoint Security Market
Market Size in USD Billion
CAGR :
% 
 USD
1.56 Billion
USD
23.19 Billion
2025
2033
USD
1.56 Billion
USD
23.19 Billion
2025
2033
| 2026 –2033 | |
| USD 1.56 Billion | |
| USD 23.19 Billion | |
|
|
|
|
What is the Global Operational Technology Endpoint Security Market Size and Growth Rate?
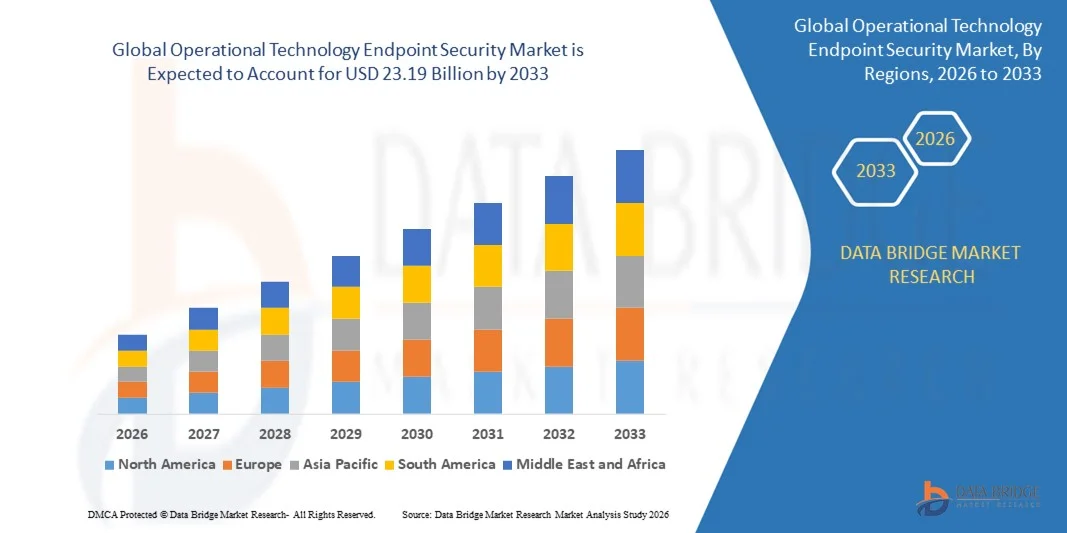
- The global operational technology endpoint security market size was valued at USD 1.56 billion in 2025 and is expected to reach USD 23.19 billion by 2033, at a CAGR of40.10% during the forecast period
- Increasing endpoint attacks and breaches is a crucial factor accelerating the market growth, also increased costs accrued due to endpoint attacks, rising demand for cost-effective alternatives for on-premises security deployment, increasing mitigation of IT risks, increasing need to manage and mitigate IT security risks, increasing popularity of the BYOD trend and rising penetration of mobile devices are the major factors among others boosting the operational technology endpoint security market
What are the Major Takeaways of Operational Technology Endpoint Security Market?
- Rising demand for securing IT infrastructure in the media and entertainment vertical and increase in demand for integrated endpoint security infrastructure and software will further create new opportunities for operational technology endpoint security market
- However, rising use of free or pirated endpoint protection solutions and rising skepticism regarding cloud-based endpoint security are the major factors among others restraining the market growth, while increasing dynamic IT infrastructure and cyber threat landscape, increasing cost of innovation and budget constraints and increasing complexity of advanced threats will further challenge the operational technology endpoint security market
- North America dominated the operational technology endpoint security market with a 43.65% revenue share in 2025, driven by strong advancements in industrial automation, critical infrastructure protection, and cybersecurity modernization across the U.S. and Canada
- Asia-Pacific is projected to register the fastest CAGR of 7.6% from 2026 to 2033, supported by rapid industrialization, robust expansion of smart manufacturing, and increasing cybersecurity awareness across China, Japan, India, South Korea, and Southeast Asia
- The On-Premise segment dominated the market with a 52.6% share in 2025, driven by its strong preference across critical infrastructure, energy, and manufacturing sectors where data sovereignty, low-latency control, and stringent compliance requirements remain essential
Report Scope and Operational Technology Endpoint Security Market Segmentation
|
Attributes |
Operational Technology Endpoint Security Key Market Insights |
|
Segments Covered |
|
|
Countries Covered |
North America
Europe
Asia-Pacific
Middle East and Africa
South America
|
|
Key Market Players |
|
|
Market Opportunities |
|
|
Value Added Data Infosets |
In addition to the insights on market scenarios such as market value, growth rate, segmentation, geographical coverage, and major players, the market reports curated by the Data Bridge Market Research also include in-depth expert analysis, pricing analysis, brand share analysis, consumer survey, demography analysis, supply chain analysis, value chain analysis, raw material/consumables overview, vendor selection criteria, PESTLE Analysis, Porter Analysis, and regulatory framework. |
What is the Key Trend in the Operational Technology Endpoint Security Market?
Increasing Integration of AI-Driven, Real-Time Threat Detection Across OT Environments
- The market is witnessing a strong shift toward AI-embedded, real-time monitoring platforms that can detect anomalies, insider threats, and advanced cyber intrusions across industrial networks
- Manufacturers are introducing lightweight, scalable, and edge-ready OT endpoint security solutions designed to protect PLCs, SCADA devices, HMIs, DCS units, and remote industrial assets
- Growing need for zero-trust frameworks, continuous device visibility, and deep packet inspection (DPI) is accelerating adoption across utilities, manufacturing, oil & gas, and transportation sectors
- For instance, leading companies such as Claroty, Nozomi Networks, Fortinet, and Cisco have enhanced their OT endpoint portfolios with improved device identification, behavioral analytics, and unified IT-OT threat intelligence capabilities
- Increasing cyberattacks targeting critical infrastructure, industrial automation systems, and connected operational assets is driving demand for next-generation endpoint defenses
- As organizations expand IIoT deployments and smart factories, OT endpoint security will remain vital for protecting critical operations, minimizing downtime, and ensuring regulatory compliance
What are the Key Drivers of Operational Technology Endpoint Security Market?
- Rising demand for secure industrial automation, driven by the integration of IIoT devices, connected sensors, and smart production systems across manufacturing and utilities
- For instance, in 2025, companies such as Palo Alto Networks, Trellix, and Check Point enhanced their OT-specific endpoint security features, including threat analytics, micro-segmentation, and hardened protection for industrial devices
- Growing frequency of ransomware attacks, supply chain vulnerabilities, and targeted intrusions across critical sectors such as energy, oil & gas, and transportation in the U.S., Europe, and Asia-Pacific
- Advancements in AI-based malware detection, network behavior monitoring, asset fingerprinting, and automated incident response have strengthened OT cybersecurity capabilities
- Rising deployment of cloud-connected OT devices, remote operations, and predictive maintenance platforms is creating the need for robust, real-time endpoint protection
- Supported by significant investments in industrial cybersecurity frameworks, modernization of infrastructure, and global compliance regulations, the OT endpoint security market is positioned for strong long-term expansion
Which Factor is Challenging the Growth of the Operational Technology Endpoint Security Market?
- High implementation and maintenance costs associated with specialized OT cybersecurity tools limit adoption among small factories, water plants, and emerging industrial zones
- For instance, during 2024–2025, rising cybersecurity talent shortages, increasing component costs, and integration complexities increased operational spending for several global end-users
- Complexity in managing mixed IT-OT environments, legacy industrial systems, and proprietary communication protocols demands advanced expertise and dedicated monitoring
- Limited awareness about OT-specific vulnerabilities, endpoint hardening techniques, and zero-trust adoption slows deployments in developing regions
- Competition from traditional IT endpoint security tools, network firewalls, and basic industrial monitoring solutions creates pricing pressure and slows differentiation
- To overcome these challenges, companies are focusing on cost-effective OT solutions, workforce training, simplified deployment models, and deeper integration with SOC platforms to accelerate global adoption of OT endpoint security
How is the Operational Technology Endpoint Security Market Segmented?
The market is segmented on the basis of deployment, end-user, enterprise, industry, and solution.
- By Deployment
The operational technology endpoint security market is segmented into On-Premise, Hybrid, and Cloud deployment models. The On-Premise segment dominated the market with a 52.6% share in 2025, driven by its strong preference across critical infrastructure, energy, and manufacturing sectors where data sovereignty, low-latency control, and stringent compliance requirements remain essential. Organizations operating legacy OT systems continue to rely on on-premise models due to limited internet exposure, high cybersecurity risks, and strict operational safety standards.
The Cloud segment is expected to grow at the fastest CAGR from 2026 to 2033, supported by rising adoption of remote monitoring, IIoT devices, connected industrial assets, and AI-based threat analytics. Increasing shift toward predictive maintenance, centralized visibility, and scalable cybersecurity architectures is pushing industries toward cloud-native security platforms that offer real-time threat intelligence, cost-efficient deployment, and simplified updates across distributed operational environments.
- By End-User
The market is segmented into Commercial and Consumer end-users. The Commercial segment dominated the market with a 68.4% share in 2025, as OT endpoint security is widely deployed across manufacturing plants, utilities, transportation networks, and industrial automation facilities. Growing cyberattacks targeting PLCs, SCADA systems, and connected operational assets are driving stronger adoption among industrial enterprises. Increasing regulatory compliance, need for asset visibility, and modernization of critical infrastructure further support segment dominance.
The Consumer segment is projected to grow at the fastest CAGR from 2026 to 2033, driven by rapid expansion of connected home devices, smart appliances, and consumer-grade IoT ecosystems. Rising concerns regarding privacy breaches, device hijacking, and home network intrusions are increasing demand for lightweight endpoint protection for smart home hubs, routers, and connected electronics. Growth in smart homes, digital lifestyles, and home automation will further accelerate consumer-level deployment.
- By Enterprise Size
The market is segmented into Large Enterprises and Small & Medium Enterprises (SMEs). Large Enterprises dominated the market with a 57.3% share in 2025, driven by high investment capacity, large-scale device networks, and stringent cybersecurity requirements across industrial production facilities, energy plants, and transportation operations. Their need for advanced threat detection, zero-trust architectures, and complex OT-IT integration further strengthens adoption.
SMEs are expected to grow at the fastest CAGR from 2026 to 2033, supported by increasing digitalization of small manufacturing units, adoption of cloud-based OT security solutions, and rising cyber risks affecting smaller industrial setups. Cost-efficient, lightweight, and easy-to-deploy security platforms are gaining traction as SMEs modernize operations and expand reliance on automation, robotics, and connected equipment. Government-led cybersecurity awareness programs also accelerate growth in this segment.
- By Industry
The market is segmented across multiple industries. The Government & Public Sector segment dominated the market with a 32.1% share in 2025, driven by the critical need to protect smart city infrastructure, defense assets, public utilities, water systems, and national-level operational networks. Rising cyberattacks targeting public infrastructure and increasing regulatory mandates continue to strengthen segment adoption.
The Healthcare segment is expected to grow at the fastest CAGR from 2026 to 2033, fueled by rising cyber threats targeting medical devices, hospital OT environments, diagnostic equipment, and connected life-support systems. Increasing digitalization of healthcare operations, remote monitoring tools, and IoMT systems fuels demand for specialized OT endpoint security. Growing compliance requirements for patient data and clinical systems further accelerate adoption across global healthcare facilities
- By Solution
The market is segmented into Endpoint Protection Platform (EPP) and Endpoint Detection & Response (EDR). The Endpoint Protection Platform segment dominated the market with a 54.7% share in 2025, as industries rely heavily on malware prevention, device control, asset visibility, and baseline protection to secure critical OT endpoints. EPP solutions remain widely adopted due to their affordability, ease of integration, and suitability for legacy OT devices with limited processing capacity.
The Endpoint Detection & Response segment is projected to grow at the fastest CAGR from 2026 to 2033, supported by growing demand for real-time monitoring, behavioral analytics, automated incident response, and advanced threat hunting. Increasing sophistication of industrial cyberattacks, including ransomware, supply-chain breaches, and zero-day exploits, is driving organizations to adopt EDR solutions that provide deeper investigation, forensic capabilities, and continuous monitoring across operational networks.
Which Region Holds the Largest Share of the Operational Technology Endpoint Security Market?
- North America dominated the operational technology endpoint security market with a 43.65% revenue share in 2025, driven by strong advancements in industrial automation, critical infrastructure protection, and cybersecurity modernization across the U.S. and Canada. High deployment of OT cybersecurity tools to secure SCADA networks, industrial control systems (ICS), and connected operational assets continues to support regional leadership
- Rapid expansion of IoT-enabled manufacturing, digital oil & gas operations, transportation automation, and smart utilities is increasing demand for endpoint protection and detection systems across industrial environments
- Robust regulatory frameworks, strong cybersecurity funding, and rising adoption of AI-driven security tools further strengthen the region’s dominance
U.S. Operational Technology Endpoint Security Market Insight
The U.S. is the largest contributor in North America, supported by strong industrial cybersecurity regulation, rapid digital transformation, and high-risk exposure across energy, utilities, aerospace, defence, and transportation sectors. Increasing deployment of OT monitoring tools, growing ICS upgrades, and rising cyberattacks targeting critical infrastructure intensify demand for advanced endpoint protection and real-time threat detection. The presence of major cybersecurity companies, strong government initiatives, and large-scale OT modernization programs further accelerates market growth.
Canada Operational Technology Endpoint Security Market Insight
Canada contributes significantly to regional expansion, driven by rising investment in critical infrastructure protection, smart grid development, and industrial automation. Increasing cyber incidents targeting utilities, manufacturing units, and transportation networks is driving higher adoption of endpoint detection, monitoring, and vulnerability management tools. Government-backed cybersecurity programs, strong R&D capabilities, and growing emphasis on securing ICS and SCADA environments reinforce long-term market adoption across the country.
Asia-Pacific Operational Technology Endpoint Security Market
Asia-Pacific is projected to register the fastest CAGR of 7.6% from 2026 to 2033, supported by rapid industrialization, robust expansion of smart manufacturing, and increasing cybersecurity awareness across China, Japan, India, South Korea, and Southeast Asia. Widespread deployment of IoT devices, factory automation equipment, industrial robots, and high-speed communication networks increases the need for strong endpoint security across OT environments. Accelerated growth in semiconductor production, EV manufacturing, and smart infrastructure projects continues to drive adoption of advanced OT cybersecurity solutions across the region.
China Operational Technology Endpoint Security Market Insight
China leads the Asia-Pacific market due to large-scale industrial automation, significant OT modernization, and high government spending on critical infrastructure security. Rising cyber threats targeting power grids, telecom networks, and manufacturing facilities are increasing demand for real-time monitoring and endpoint protection. Strong local cybersecurity ecosystem and expanding 5G and industrial IoT deployments further support rapid market adoption.
Japan Operational Technology Endpoint Security Market Insight
Japan shows steady growth driven by mature manufacturing ecosystems, strong robotics integration, and modernization of industrial control systems. High cybersecurity standards, increasing adoption of digital factories, and strong focus on system reliability contribute to growing demand for advanced OT endpoint protection tools. Expansion in automotive electronics, precision manufacturing, and smart infrastructure further strengthens long-term market growth.
India Operational Technology Endpoint Security Market Insight
India is emerging as a fast-growing market supported by rapid industrial digitalization, expansion of smart manufacturing facilities, and rising cybersecurity investments across energy, transportation, and telecom sectors. Government programs promoting industrial automation, smart cities, and digital infrastructure accelerate deployment of OT security tools. Increasing cyberattacks against critical infrastructure also drives widespread adoption.
South Korea Operational Technology Endpoint Security Market Insight
South Korea contributes significantly due to strong demand for OT security across semiconductor manufacturing, automotive electronics, telecom, and industrial automation sectors. High deployment of 5G networks, AI-driven systems, and connected factories intensifies demand for robust endpoint protection. With advanced technological capabilities and strong industrial cybersecurity awareness, South Korea continues to exhibit solid market growth.
Which are the Top Companies in Operational Technology Endpoint Security Market?
The operational technology endpoint security industry is primarily led by well-established companies, including:
- Microsoft (U.S.)
- CrowdStrike (U.S.)
- Symantec Corporation (U.S.)
- Trend Micro Incorporated (Japan)
- Sophos Ltd (U.K.)
- McAfee, LLC (U.S.)
- AO Kaspersky Lab (Russia)
- VMware, Inc. (U.S.)
- SentinelOne (U.S.)
- ESET (Slovakia)
- Cylance Inc (U.S.)
- Bitdefender (Romania)
- Cisco Systems (U.S.)
- FireEye, Inc. (U.S.)
- Panda Security (Spain)
- F-Secure (Finland)
- Palo Alto Networks (U.S.)
- Check Point Software Technologies Ltd. (Israel)
- Fortinet, Inc. (U.S.)
- Malwarebytes (U.S.)
- Comodo Security Solutions, Inc. (U.S.)
What are the Recent Developments in Global Operational Technology Endpoint Security Market?
- In February 2025, Check Point entered into a strategic partnership with cloud security firm Wiz to enhance enterprise protection across hybrid cloud environments. This collaboration integrates cloud network security with Cloud Native Application Protection (CNAPP) to deliver a unified and holistic security framework. This move strengthens both companies’ positions in providing end-to-end cloud security
- In January 2025, Tenable finalized an agreement to acquire Vulcan Cyber, a leading exposure management provider, enabling seamless integration of Vulcan’s capabilities into Tenable’s platform. This enhancement helps organizations consolidate vulnerabilities, prioritize cybersecurity risks, and accelerate remediation efforts across the attack surface. This acquisition marks a strategic expansion of Tenable’s exposure management capabilities
- In July 2024, CyberKnight formed a partnership with Forescout to deliver comprehensive asset intelligence and control spanning IT, OT, and IoT systems in the META region. This collaboration supports enterprises transitioning to cloud environments by providing greater visibility into their digital infrastructure. This partnership reinforces CyberKnight’s portfolio in multi-domain security intelligence
- In March 2024, C-DOT collaborated with PRL to integrate fiber-based OT security technology with free-space OT security systems, establishing India’s first hybrid quantum communication link. This achievement combines fiber and free-space channels to enhance secure communication capabilities. This collaboration represents a major technological milestone for India's quantum communication ecosystem
- In April 2023, Trellix introduced the Trellix Endpoint Security Suite designed to provide SOC teams with improved endpoint visibility and centralized control. The suite offers advanced monitoring and proactive defense features through a unified interface. This launch strengthens Trellix’s position in next-generation endpoint security solutions
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.