Global Security Policy Management Market
Market Size in USD Billion
CAGR :
% 
 USD
2.45 Billion
USD
7.98 Billion
2024
2032
USD
2.45 Billion
USD
7.98 Billion
2024
2032
| 2025 –2032 | |
| USD 2.45 Billion | |
| USD 7.98 Billion | |
|
|
|
|
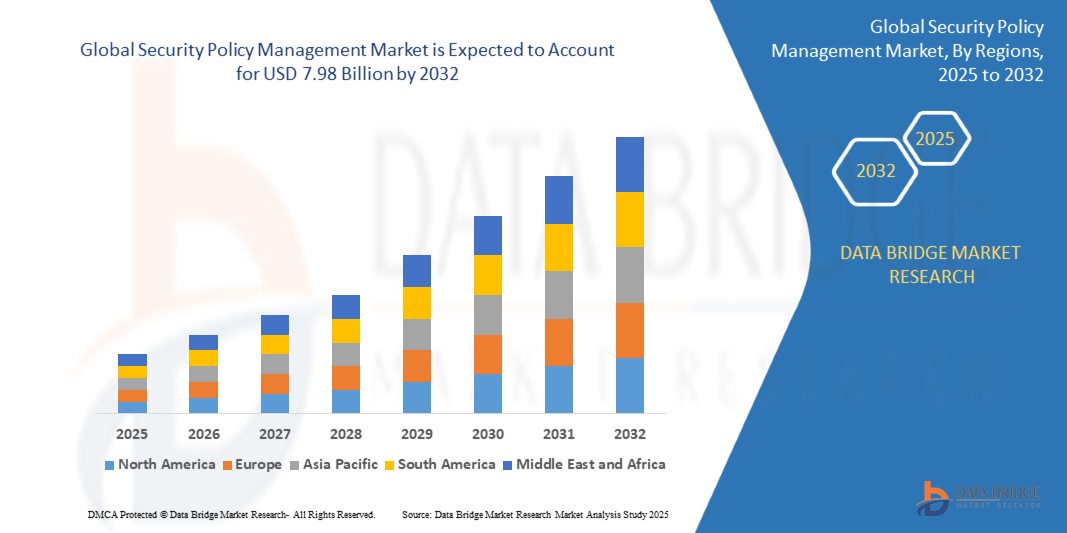
Security Policy Management Market Size
- The Global Security Policy Management Market was valued at USD 2.45 billion in 2024 and is projected to reach USD 7.98 billion by 2032, growing at a CAGR of 18.38% during the forecast period.
- Growth is driven by increasing complexities in network infrastructure, rising cyber threats, and growing adoption of multi-cloud and hybrid IT environments, necessitating centralized and automated security policy enforcement.
Security Policy Management Market Analysis
- Security policy management refers to platforms and tools that automate, standardize, and enforce security rules, firewall policies, and access controls across a diverse and distributed IT environment.
- The need for real-time policy updates, regulatory compliance, and risk mitigation is pushing enterprises to adopt policy orchestration platforms integrated with firewalls, cloud access security brokers (CASBs), and SD-WANs.
- As organizations shift toward zero-trust architectures and cloud-native applications, security policy management becomes critical for maintaining consistent security posture and streamlining audits.
- The integration of AI and ML algorithms in policy engines is enabling dynamic, risk-aware decision-making for access control and threat response, improving policy accuracy and automation.
- Industry sectors such as banking, telecom, and healthcare are prioritizing security policy automation to cope with the proliferation of endpoints, IoT devices, and third-party access points.
Report Scope and Security Policy Management Market Segmentation
|
Attributes |
Security Policy Management Market Key Market Insights |
|
Segments Covered |
|
|
Countries Covered |
North America
Europe
Asia-Pacific
Middle East and Africa
South America
|
|
Key Market Players |
|
|
Market Opportunities |
|
|
Value Added Data Infosets |
In addition to the insights on market scenarios such as market value, growth rate, segmentation, geographical coverage, and major players, the market reports curated by the Data Bridge Market Research also include import export analysis, production capacity overview, production consumption analysis, price trend analysis, climate change scenario, supply chain analysis, value chain analysis, raw material/consumables overview, vendor selection criteria, PESTLE Analysis, Porter Analysis, and regulatory framework. |
Security Policy Management Market Trends
Automation, Cloud Governance, and Zero Trust Integration Drive Policy Management Evolution
- Rise of Automated Policy Orchestration: Organizations are adopting AI-powered orchestration engines to automate rule creation, enforce compliance, and eliminate manual errors in complex, multi-vendor environments.
- Policy-as-Code in DevSecOps Pipelines: Developers and security teams are embedding security policies directly into CI/CD workflows, enabling early risk detection and shift-left security enforcement.
- Adoption of Unified Security Platforms: Enterprises are migrating to consolidated security frameworks that unify firewall, access, endpoint, and cloud policies through a centralized management console.
- Real-Time Threat-Driven Policy Adjustments: Integration of SIEM and SOAR platforms with policy managers allows for dynamic policy updates based on threat intelligence and behavioral analysis.
- Zero Trust Network Access (ZTNA) Acceleration: Security policy management is becoming a cornerstone for ZTNA strategies, ensuring least privilege access, identity verification, and continuous trust assessment.
Security Policy Management Market Dynamics
Driver
Complex Threat Landscape and Distributed IT Environments Demand Centralized Policy Governance
- With rising ransomware, insider threats, and APTs, enterprises need real-time enforcement of security policies across distributed and hybrid infrastructures.
- Organizations are facing compliance burdens with evolving regulatory standards (GDPR, HIPAA, ISO 27001), increasing the urgency for automated audit trails and centralized rule engines.
- The widespread adoption of multi-cloud platforms, remote work, and BYOD policies has made it difficult to enforce consistent security postures—driving adoption of cloud-native policy management.
- Digital transformation initiatives in BFSI, telecom, and healthcare have increased exposure to external and internal threats, highlighting the need for centralized, scalable, and policy-aware security architectures.
Restraint/Challenge
Integration Complexity and Lack of Skilled Security Policy Professionals
- Many organizations operate with disparate security tools across endpoints, firewalls, cloud, and identity systems—creating integration challenges and policy silos.
- Lack of skilled personnel who can interpret compliance frameworks, optimize policy logic, and manage multi-environment enforcement slows down adoption of advanced platforms.
- Ensuring compatibility between legacy systems and modern orchestration tools can lead to misconfigurations or network disruptions.
- Continuous tuning of policies to avoid false positives, redundant rules, or conflicting exceptions is resource-intensive and requires ongoing governance alignment.
Security Policy Management Market Scope
The market is segmented based on component, deployment mode, enterprise size, and end user, reflecting the evolving threat landscape and security needs across industries.
- By Component
Segmented into Solutions and Services. Solutions lead the market in 2025, driven by demand for policy automation platforms, firewall management tools, and network access control software. The services segment is expected to grow rapidly due to increasing need for policy consulting, risk assessments, and managed security services (MSS).
- By Deployment Mode
Segmented into On-Premise and Cloud-Based. Cloud-based deployment dominates in 2025, supported by the rise of SaaS models, multi-cloud environments, and remote workforces. On-premise remains relevant in regulated industries requiring greater control over data and infrastructure.
- By Enterprise Size
Includes Large Enterprises and Small & Medium-sized Enterprises (SMEs). Large enterprises dominate due to complex IT landscapes and high compliance demands. However, SMEs are showing strong adoption growth as affordable, cloud-native policy tools become more available.
- By End User
Key industries include BFSI, IT & Telecom, Healthcare, Retail & eCommerce, Government & Defense, Energy & Utilities, and Others. BFSI leads in 2025 due to strict compliance regulations and the critical nature of financial data. The IT & Telecom segment follows closely, driven by 5G rollout, network virtualization, and cloud integration.
Security Policy Management Market Regional Analysis
- North America dominates in 2025, driven by strong demand from BFSI, government, and IT services sectors. The U.S. leads with high adoption of zero-trust architectures, cloud migration, and cyber regulations enforcement.
- Europe is growing steadily, supported by GDPR and strong adoption across banking, defense, and critical infrastructure. Countries like Germany, the U.K., and France prioritize policy compliance, cloud security orchestration, and data privacy enforcement.
- Asia-Pacific is the fastest-growing region due to rapid digitalization, cybersecurity modernization, and regulatory mandates in India, China, South Korea, and Australia. Enterprises are investing in scalable and cost-efficient policy platforms amid increasing cyber threats.
- Middle East & Africa (MEA) sees growing demand for policy management solutions in government and energy sectors, particularly in UAE, Saudi Arabia, and South Africa, as they enhance national cybersecurity capabilities.
- South America, especially Brazil and Mexico, is deploying policy management tools in financial, telecom, and public sectors, supported by data protection regulations and modernization of IT security infrastructure.
United States
The U.S. leads in adoption due to robust demand across federal agencies, large enterprises, and financial institutions. The focus is on zero-trust policy frameworks, cloud access controls, and automated audit tools.
Germany
Germany drives policy enforcement in automotive, manufacturing, and banking sectors, with a strong emphasis on GDPR compliance, data sovereignty, and multi-cloud security governance.
India
India is rapidly adopting cloud-native and AI-integrated policy tools across IT, eCommerce, and public infrastructure, aided by Digital India, data localization rules, and increasing cyberattack awareness.
China
China is scaling policy enforcement across state-owned enterprises, telcos, and smart city infrastructure, aligning with national cybersecurity compliance mandates and 5G rollouts.
Brazil
Brazil is focusing on security policy unification across finance, telecom, and healthcare, particularly after the implementation of LGPD (General Data Protection Law), driving policy visibility and change automation.
Security Policy Management Market Share
The Security Policy Management industry is primarily led by well-established companies, including:
- Cisco Systems, Inc. (U.S.)
- McAfee, LLC (U.S.)
- Palo Alto Networks, Inc. (U.S.)
- Check Point Software Technologies Ltd. (Israel)
- Fortinet, Inc. (U.S.)
- FireMon LLC (U.S.)
- AlgoSec Inc. (U.S.)
- Juniper Networks, Inc. (U.S.)
- Tufin Software Technologies Ltd. (Israel)
- Sophos Group plc (U.K.)
- IBM Corporation (U.S.)
Latest Developments in Global Security Policy Management Market
- In April 2025, Palo Alto Networks introduced its AI-enhanced policy automation engine within its Prisma Cloud suite, enabling real-time enforcement of security policies across hybrid and multi-cloud environments with built-in compliance tracking.
- In March 2025, Cisco Systems launched a Zero Trust Policy Management Toolkit integrated with Cisco SecureX, designed to simplify micro-segmentation, access policy updates, and incident response within zero-trust frameworks.
- In February 2025, AlgoSec released an upgraded version of its FireFlow solution with advanced support for policy-as-code, allowing DevSecOps teams to embed security policies directly into CI/CD pipelines.
- In January 2025, FireMon LLC announced its Cloud Security Operations Center (CloudSOC), a unified policy visualization and governance dashboard for managing policies across AWS, Azure, and GCP simultaneously.
- In December 2024, Fortinet integrated adaptive security policies into its FortiOS 8.0 platform, enabling context-aware policy enforcement based on user behavior, device posture, and real-time threat intelligence.
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Table of Content
1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GLOBAL SECURITY POLICY MANAGEMENT MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATION
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 KEY TAKEAWAYS
2.2 ARRIVING AT THE GLOBAL SECURITY POLICY MANAGEMENT MARKET
2.2.1 VENDOR POSITIONING GRID
2.2.2 TECHNOLOGY LIFE LINE CURVE
2.2.3 MARKET GUIDE
2.2.4 COMPANY POSITIONING GRID
2.2.5 MULTIVARIATE MODELLING
2.2.6 STANDARDS OF MEASUREMENT
2.2.7 TOP TO BOTTOM ANALYSIS
2.2.8 VENDOR SHARE ANALYSIS
2.2.9 DATA POINTS FROM KEY PRIMARY INTERVIEWS
2.2.10 DATA POINTS FROM KEY SECONDARY DATABASES
2.3 GLOBAL SECURITY POLICY MANAGEMENT MARKET: RESEARCH SNAPSHOT
2.4 ASSUMPTIONS
3 MARKET OVERVIEW
3.1 DRIVERS
3.2 RESTRAINTS
3.3 OPPORTUNITIES
3.4 CHALLENGES
4 EXECUTIVE SUMMARY
5 PREMIUM INSIGHTS
5.1 CASE STUDIES
5.2 REGULATORY FRAMEWORK
5.3 TECHNOLOGICAL TRENDS
5.4 PRICING ANALYSIS
5.5 VALUE CHAIN ANALYSIS
6 GLOBAL SECURITY POLICY MANAGEMENT MARKET, BY PRODUCT TYPE
6.1 OVERVIEW
6.2 NETWORK POLICY MANAGEMENT
6.3 CHANGE MANAGEMENT
6.4 COMPLIANCE & AUDITING
6.5 VULNERABILITY ASSESSMENT
7 GLOBAL SECURITY POLICY MANAGEMENT MARKET, BY OFFERING
7.1 OVERVIEW
7.2 SOLUTIONS
7.3 SERVICES
7.3.1 PROFESSIONAL SERVICES
7.3.1.1. CONSULTING
7.3.1.2. IMPLEMENTATION & INTEGRATION
7.3.1.3. SUPPORT & MAINTENANCE
7.3.2 MANAGED SERVICES
8 GLOBAL SECURITY POLICY MANAGEMENT MARKET, BY ORGANIZATION SIZE
8.1 OVERVIEW
8.2 SMALL SCALE ORGANIZATIONS
8.3 MEDIUM SCALE ORGANIZATIONS
8.4 LARGE SCALE ORGANIZATIONS
9 GLOBAL SECURITY POLICY MANAGEMENT MARKET, BY DEPLOYMENT MODE
9.1 OVERVIEW
9.2 ON-PREMISE
9.3 CLOUD
10 GLOBAL SECURITY POLICY MANAGEMENT MARKET, BY END USER
10.1 OVERVIEW
10.2 BFSI
10.2.1 BY PRODUCT TYPE
10.2.1.1. NETWORK POLICY MANAGEMENT
10.2.1.2. CHANGE MANAGEMENT
10.2.1.3. COMPLIANCE & AUDITING
10.2.1.4. VULNERABILITY ASSESSMENT
10.3 IT & TELECOM
10.3.1 BY PRODUCT TYPE
10.3.1.1. NETWORK POLICY MANAGEMENT
10.3.1.2. CHANGE MANAGEMENT
10.3.1.3. COMPLIANCE & AUDITING
10.3.1.4. VULNERABILITY ASSESSMENT
10.4 HEALTHCARE
10.4.1 BY PRODUCT TYPE
10.4.1.1. NETWORK POLICY MANAGEMENT
10.4.1.2. CHANGE MANAGEMENT
10.4.1.3. COMPLIANCE & AUDITING
10.4.1.4. VULNERABILITY ASSESSMENT
10.5 MANUFACTURING
10.5.1 BY PRODUCT TYPE
10.5.1.1. NETWORK POLICY MANAGEMENT
10.5.1.2. CHANGE MANAGEMENT
10.5.1.3. COMPLIANCE & AUDITING
10.5.1.4. VULNERABILITY ASSESSMENT
10.6 ENERGY & UTILITIES
10.6.1 BY PRODUCT TYPE
10.6.1.1. NETWORK POLICY MANAGEMENT
10.6.1.2. CHANGE MANAGEMENT
10.6.1.3. COMPLIANCE & AUDITING
10.6.1.4. VULNERABILITY ASSESSMENT
10.7 GOVERNMENT
10.7.1 BY PRODUCT TYPE
10.7.1.1. NETWORK POLICY MANAGEMENT
10.7.1.2. CHANGE MANAGEMENT
10.7.1.3. COMPLIANCE & AUDITING
10.7.1.4. VULNERABILITY ASSESSMENT
10.8 MANUFACTURING
10.8.1 BY PRODUCT TYPE
10.8.1.1. NETWORK POLICY MANAGEMENT
10.8.1.2. CHANGE MANAGEMENT
10.8.1.3. COMPLIANCE & AUDITING
10.8.1.4. VULNERABILITY ASSESSMENT
10.9 RETAIL
10.9.1 BY PRODUCT TYPE
10.9.1.1. NETWORK POLICY MANAGEMENT
10.9.1.2. CHANGE MANAGEMENT
10.9.1.3. COMPLIANCE & AUDITING
10.9.1.4. VULNERABILITY ASSESSMENT
10.1 OTHERS
10.10.1 BY PRODUCT TYPE
10.10.1.1. NETWORK POLICY MANAGEMENT
10.10.1.2. CHANGE MANAGEMENT
10.10.1.3. COMPLIANCE & AUDITING
10.10.1.4. VULNERABILITY ASSESSMENT
11 GLOBAL SECURITY POLICY MANAGEMENT MARKET, BY REGION
11.1 GLOBAL SECURITY POLICY MANAGEMENT MARKET, (ALL SEGMENTATION PROVIDED ABOVE IS REPRESENTED IN THIS CHAPTER BY COUNTRY)
11.2 NORTH AMERICA
11.2.1 U.S.
11.2.2 CANADA
11.2.3 MEXICO
11.3 EUROPE
11.3.1 GERMANY
11.3.2 FRANCE
11.3.3 U.K.
11.3.4 ITALY
11.3.5 SPAIN
11.3.6 RUSSIA
11.3.7 TURKEY
11.3.8 BELGIUM
11.3.9 NETHERLANDS
11.3.10 SWITZERLAND
11.3.11 REST OF EUROPE
11.4 ASIA PACIFIC
11.4.1 JAPAN
11.4.2 CHINA
11.4.3 SOUTH KOREA
11.4.4 INDIA
11.4.5 AUSTRALIA
11.4.6 SINGAPORE
11.4.7 THAILAND
11.4.8 MALAYSIA
11.4.9 INDONESIA
11.4.10 PHILIPPINES
11.4.11 REST OF ASIA PACIFIC
11.5 SOUTH AMERICA
11.5.1 BRAZIL
11.5.2 ARGENTINA
11.5.3 REST OF SOUTH AMERICA
11.6 MIDDLE EAST AND AFRICA
11.6.1 SOUTH AFRICA
11.6.2 EGYPT
11.6.3 SAUDI ARABIA
11.6.4 U.A.E
11.6.5 ISRAEL
11.6.6 REST OF MIDDLE EAST AND AFRICA
12 GLOBAL SECURITY POLICY MANAGEMENT MARKET,COMPANY LANDSCAPE
12.1 COMPANY SHARE ANALYSIS: GLOBAL
12.2 COMPANY SHARE ANALYSIS: NORTH AMERICA
12.3 COMPANY SHARE ANALYSIS: EUROPE
12.4 COMPANY SHARE ANALYSIS: ASIA-PACIFIC
12.5 MERGERS & ACQUISITIONS
12.6 NEW PRODUCT DEVELOPMENT AND APPROVALS
12.7 EXPANSIONS
12.8 REGULATORY CHANGES
12.9 PARTNERSHIP AND OTHER STRATEGIC DEVELOPMENTS
13 GLOBAL SECURITY POLICY MANAGEMENT MARKET, SWOT AND DBMR ANALYSIS
14 GLOBAL SECURITY POLICY MANAGEMENT MARKET, COMPANY PROFILE
14.1 JUNIPER NETWORKS
14.1.1 COMPANY SNAPSHOT
14.1.2 REVENUE ANALYSIS
14.1.3 GEOGRAPHIC PRESENCE
14.1.4 PRODUCT PORTFOLIO
14.1.5 RECENT DEVELOPMENTS
14.2 SAP
14.2.1 COMPANY SNAPSHOT
14.2.2 REVENUE ANALYSIS
14.2.3 GEOGRAPHIC PRESENCE
14.2.4 PRODUCT PORTFOLIO
14.2.5 RECENT DEVELOPMENTS
14.3 PALO ALTO NETWORKS
14.3.1 COMPANY SNAPSHOT
14.3.2 REVENUE ANALYSIS
14.3.3 GEOGRAPHIC PRESENCE
14.3.4 PRODUCT PORTFOLIO
14.3.5 RECENT DEVELOPMENTS
14.4 CHECK POINT SOFTWARE TECHNOLOGY
14.4.1 COMPANY SNAPSHOT
14.4.2 REVENUE ANALYSIS
14.4.3 GEOGRAPHIC PRESENCE
14.4.4 PRODUCT PORTFOLIO
14.4.5 RECENT DEVELOPMENTS
14.5 MICRO FOCUS CORPORATION
14.5.1 COMPANY SNAPSHOT
14.5.2 REVENUE ANALYSIS
14.5.3 GEOGRAPHIC PRESENCE
14.5.4 PRODUCT PORTFOLIO
14.5.5 RECENT DEVELOPMENTS
14.6 CISCO, INC
14.6.1 COMPANY SNAPSHOT
14.6.2 REVENUE ANALYSIS
14.6.3 GEOGRAPHIC PRESENCE
14.6.4 PRODUCT PORTFOLIO
14.6.5 RECENT DEVELOPMENTS
14.7 IBM CORPORATION
14.7.1 COMPANY SNAPSHOT
14.7.2 REVENUE ANALYSIS
14.7.3 GEOGRAPHIC PRESENCE
14.7.4 PRODUCT PORTFOLIO
14.7.5 RECENT DEVELOPMENTS
14.8 SKYBOX SECURITY
14.8.1 COMPANY SNAPSHOT
14.8.2 REVENUE ANALYSIS
14.8.3 GEOGRAPHIC PRESENCE
14.8.4 PRODUCT PORTFOLIO
14.8.5 RECENT DEVELOPMENTS
14.9 OPAQ NETWORKS
14.9.1 COMPANY SNAPSHOT
14.9.2 REVENUE ANALYSIS
14.9.3 GEOGRAPHIC PRESENCE
14.9.4 PRODUCT PORTFOLIO
14.9.5 RECENT DEVELOPMENTS
14.1 ENTERPRISE INTEGRATION
14.10.1 COMPANY SNAPSHOT
14.10.2 REVENUE ANALYSIS
14.10.3 GEOGRAPHIC PRESENCE
14.10.4 PRODUCT PORTFOLIO
14.10.5 RECENT DEVELOPMENTS
14.11 CONETRIX
14.11.1 COMPANY SNAPSHOT
14.11.2 REVENUE ANALYSIS
14.11.3 GEOGRAPHIC PRESENCE
14.11.4 PRODUCT PORTFOLIO
14.11.5 RECENT DEVELOPMENTS
14.12 ODYSSEY CONSULTANTS
14.12.1 COMPANY SNAPSHOT
14.12.2 REVENUE ANALYSIS
14.12.3 GEOGRAPHIC PRESENCE
14.12.4 PRODUCT PORTFOLIO
14.12.5 RECENT DEVELOPMENTS
14.13 IMANAGE
14.13.1 COMPANY SNAPSHOT
14.13.2 REVENUE ANALYSIS
14.13.3 GEOGRAPHIC PRESENCE
14.13.4 PRODUCT PORTFOLIO
14.13.5 RECENT DEVELOPMENTS
14.14 TUFIN CORPORATION
14.14.1 COMPANY SNAPSHOT
14.14.2 REVENUE ANALYSIS
14.14.3 GEOGRAPHIC PRESENCE
14.14.4 PRODUCT PORTFOLIO
14.14.5 RECENT DEVELOPMENTS
14.15 MCAFEE CORPORATION
14.15.1 COMPANY SNAPSHOT
14.15.2 REVENUE ANALYSIS
14.15.3 GEOGRAPHIC PRESENCE
14.15.4 PRODUCT PORTFOLIO
14.15.5 RECENT DEVELOPMENTS
14.16 ALGOSEC
14.16.1 COMPANY SNAPSHOT
14.16.2 REVENUE ANALYSIS
14.16.3 GEOGRAPHIC PRESENCE
14.16.4 PRODUCT PORTFOLIO
14.16.5 RECENT DEVELOPMENTS
14.17 FIREMON, LLC
14.17.1 COMPANY SNAPSHOT
14.17.2 REVENUE ANALYSIS
14.17.3 GEOGRAPHIC PRESENCE
14.17.4 PRODUCT PORTFOLIO
14.17.5 RECENT DEVELOPMENTS
14.18 ITNS CONSULTING
14.18.1 COMPANY SNAPSHOT
14.18.2 REVENUE ANALYSIS
14.18.3 GEOGRAPHIC PRESENCE
14.18.4 PRODUCT PORTFOLIO
14.18.5 RECENT DEVELOPMENTS
14.19 HELPSYSTEMS
14.19.1 COMPANY SNAPSHOT
14.19.2 REVENUE ANALYSIS
14.19.3 GEOGRAPHIC PRESENCE
14.19.4 PRODUCT PORTFOLIO
14.19.5 RECENT DEVELOPMENTS
14.2 AWS GROUP
14.20.1 COMPANY SNAPSHOT
14.20.2 REVENUE ANALYSIS
14.20.3 GEOGRAPHIC PRESENCE
14.20.4 PRODUCT PORTFOLIO
14.20.5 RECENT DEVELOPMENTS
NOTE: THE COMPANIES PROFILED IS NOT EXHAUSTIVE LIST AND IS AS PER OUR PREVIOUS CLIENT REQUIREMENT. WE PROFILE MORE THAN 100 COMPANIES IN OUR STUDIES AND HENCE THE LIST OF COMPANIES CAN BE MODIFIED OR REPLACED ON REQUEST.
15 CONCLUSION
16 QUESTIONNAIRE
17 RELATED REPORTS
18 ABOUT DATA BRIDGE MARKET RESEARCH
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.