Global Security Policy Management Zero Trust Security Market
Market Size in USD Billion
CAGR :
% 
 USD
42.04 Billion
USD
130.42 Billion
2025
2033
USD
42.04 Billion
USD
130.42 Billion
2025
2033
| 2026 –2033 | |
| USD 42.04 Billion | |
| USD 130.42 Billion | |
|
|
|
|
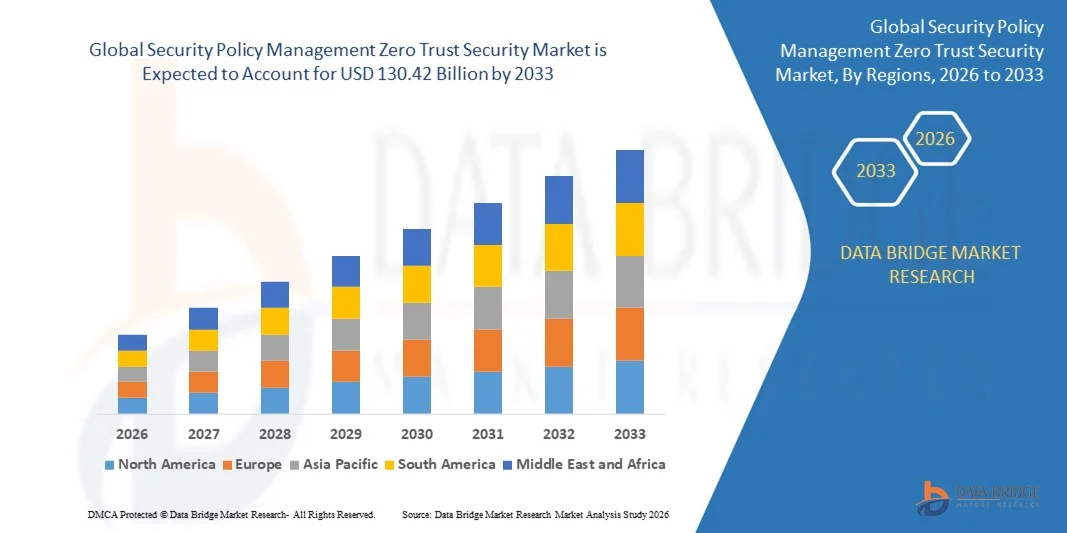
Global Security Policy Management Zero Trust Security Market Size
- The global Security Policy Management Zero Trust Security Market size was valued at USD 42.04 billion in 2025 and is projected to reach USD 130.42 billion by 2033, growing at a CAGR of 15.20% during the forecast period.
- The market expansion is primarily driven by increasing adoption of cloud-based infrastructures, enterprise mobility, and advanced cybersecurity frameworks, prompting organizations to implement robust zero trust security models.
- Additionally, growing regulatory compliance requirements, rising cyber threats, and the demand for secure, seamless, and scalable IT environments are reinforcing the need for comprehensive security policy management solutions. These factors collectively are accelerating the deployment of zero trust architectures, thereby propelling market growth.
Global Security Policy Management Zero Trust Security Market Analysis
- Zero Trust Security solutions, providing continuous verification and granular access control for users, devices, and applications, are becoming essential components of modern enterprise cybersecurity frameworks in both corporate and government settings due to their ability to reduce breach risks, enforce least-privilege access, and integrate seamlessly with existing IT infrastructure.
- The growing demand for Zero Trust Security is primarily driven by the increasing frequency and sophistication of cyberattacks, widespread adoption of cloud services, and the need for secure remote work environments.
- North America dominated the Global Security Policy Management Zero Trust Security Market with the largest revenue share of 33% in 2025, fueled by early adoption of advanced cybersecurity frameworks, stringent regulatory standards, and the presence of leading technology providers, with the U.S. witnessing substantial growth in zero trust deployments across enterprises, government agencies, and critical infrastructure sectors.
- Asia-Pacific is expected to be the fastest-growing region in the Global Security Policy Management Zero Trust Security Market during the forecast period due to rapid digital transformation, increasing enterprise IT spending, and heightened awareness of cybersecurity threats.
- The multi-factor authentication segment dominated the market with a revenue share of 58.4% in 2025, driven by increasing cybersecurity threats and regulatory compliance requirements that mandate stronger identity verification.
Report Scope and Global Security Policy Management Zero Trust Security Market Segmentation
|
Attributes |
Security Policy Management Zero Trust Security Key Market Insights |
|
Segments Covered |
|
|
Countries Covered |
North America
Europe
Asia-Pacific
Middle East and Africa
South America
|
|
Key Market Players |
• Cisco Systems (U.S.) |
|
Market Opportunities |
|
|
Value Added Data Infosets |
In addition to the market insights such as market value, growth rate, market segments, geographical coverage, market players, and market scenario, the market report curated by the Data Bridge Market Research team includes in-depth expert analysis, import/export analysis, pricing analysis, production consumption analysis, and pestle analysis. |
Global Security Policy Management Zero Trust Security Market Trends
Enhanced Security and Automation Through AI and Machine Learning Integration
- A significant and accelerating trend in the global Security Policy Management Zero Trust Security Market is the deepening integration of artificial intelligence (AI) and machine learning (ML) with security policy management and zero trust frameworks. This convergence is enabling more intelligent threat detection, automated policy enforcement, and adaptive access controls, significantly enhancing organizational cybersecurity posture.
- For instance, platforms such as Palo Alto Networks’ Prisma Access and Cisco Zero Trust leverage AI-driven analytics to continuously monitor user behavior, detect anomalies, and automatically adjust access privileges, reducing the risk of breaches. Similarly, Okta Identity Cloud uses machine learning to identify risky login patterns and prompt step-up authentication only when necessary, balancing security with user convenience.
- AI integration in zero trust architectures allows predictive threat detection, automated response to suspicious activity, and intelligent policy recommendations. For example, CrowdStrike Falcon employs ML to analyze endpoint behavior in real time, while AI-powered identity and access management systems can dynamically adapt permissions based on contextual risk factors.
- The seamless integration of AI and ML with zero trust frameworks facilitates centralized management across complex IT environments. Organizations can monitor access controls, endpoint security, cloud applications, and network activity from a single interface, enabling comprehensive visibility and automated enforcement of security policies.
- This trend toward more intelligent, adaptive, and automated security systems is reshaping enterprise expectations for cybersecurity. Consequently, companies such as Zscaler, Fortinet, and Microsoft are developing AI-enabled solutions with features such as continuous risk assessment, automated threat remediation, and adaptive access management based on real-time analytics.
- The demand for zero trust security solutions enhanced with AI and machine learning is growing rapidly across enterprise, government, and critical infrastructure sectors, as organizations increasingly prioritize proactive threat mitigation, operational efficiency, and streamlined security management.
Global Security Policy Management Zero Trust Security Market Dynamics
Driver
Growing Need Due to Rising Cybersecurity Threats and Digital Transformation
- The increasing prevalence of sophisticated cyberattacks, data breaches, and regulatory compliance requirements, coupled with accelerating digital transformation initiatives across enterprises, is a significant driver for the heightened demand for Zero Trust Security solutions.
- For instance, in 2025, Microsoft expanded its Zero Trust capabilities within Microsoft 365 and Azure, integrating AI-driven identity protection and conditional access policies to safeguard cloud and on-premises environments. Such initiatives by leading companies are expected to propel market growth during the forecast period.
- As organizations become more aware of evolving security threats and the limitations of traditional perimeter-based defenses, Zero Trust architectures offer advanced features such as continuous verification, adaptive access policies, and real-time threat monitoring, providing a compelling upgrade over legacy security frameworks.
- Furthermore, the growing adoption of cloud services, remote work models, and interconnected enterprise systems is making Zero Trust Security an integral component of modern IT environments, ensuring seamless protection across networks, applications, and endpoints.
- The ability to enforce least-privilege access, monitor user behavior, and respond dynamically to potential threats are key factors driving the adoption of Zero Trust solutions across enterprises, government agencies, and critical infrastructure sectors. The trend toward scalable, policy-driven security management and the increasing availability of user-friendly platforms further contribute to market growth.
Restraint/Challenge
Concerns Regarding Implementation Complexity and High Initial Costs
- Challenges surrounding the complexity of implementing Zero Trust Security frameworks, along with the high initial costs of deployment, pose barriers to broader market adoption. Deploying comprehensive Zero Trust solutions often requires integration across multiple IT systems, identity platforms, and endpoints, which can be resource-intensive.
- For instance, smaller enterprises or organizations with legacy IT infrastructure may face difficulties in adopting full-scale Zero Trust solutions due to technical and financial constraints.
- Addressing these challenges through simplified deployment models, managed Zero Trust services, and scalable subscription-based offerings is crucial for encouraging adoption. Companies such as Zscaler, Okta, and Palo Alto Networks emphasize cloud-native deployment options, stepwise implementation strategies, and flexible pricing to reduce entry barriers for organizations.
- While ongoing cost reductions and improved deployment frameworks are easing adoption, the perceived complexity and premium associated with advanced Zero Trust Security solutions can still hinder uptake, particularly among small and mid-sized enterprises or cost-sensitive sectors.
- Overcoming these challenges through comprehensive implementation guidance, robust vendor support, and education on the long-term ROI of Zero Trust Security will be vital for sustained market growth.
Global Security Policy Management Zero Trust Security Market Scope
Security policy management zero trust security market is segmented on the basis of authentication type, deployment, organization size and vertical.
- By Authentication Type
On the basis of authentication type, the Global Security Policy Management Zero Trust Security Market is segmented into single-factor authentication (SFA) and multi-factor authentication (MFA). The multi-factor authentication segment dominated the market with a revenue share of 58.4% in 2025, driven by increasing cybersecurity threats and regulatory compliance requirements that mandate stronger identity verification. MFA enhances security by combining two or more credentials, such as passwords, biometrics, and security tokens, significantly reducing the risk of unauthorized access. Enterprises and government organizations are increasingly deploying MFA to protect critical systems, cloud applications, and sensitive data.
The single-factor authentication segment is expected to witness the fastest CAGR of 19.8% from 2026 to 2033, fueled by growing adoption in SMEs and organizations seeking simpler, cost-effective solutions for securing basic applications, especially in regions where cyber risk awareness is rising gradually.
- By Deployment
On the basis of deployment, the Global Security Policy Management Zero Trust Security Market is segmented into on-premises and cloud-based solutions. The cloud segment dominated the market with a revenue share of 62.1% in 2025, driven by the widespread adoption of cloud infrastructures, remote work trends, and the scalability and flexibility offered by cloud-native zero trust platforms. Cloud deployments enable real-time monitoring, centralized policy management, and seamless integration with SaaS applications, making them particularly attractive for enterprises with distributed operations.
The on-premises segment is expected to witness the fastest CAGR of 18.5% from 2026 to 2033, supported by industries with strict data privacy or regulatory mandates, such as government and defense, which prefer local control over sensitive systems while gradually integrating hybrid zero trust frameworks.
- By Organization Size
On the basis of organization size, the Global Security Policy Management Zero Trust Security Market is segmented into SMEs and large enterprises. The large enterprise segment dominated the market with a revenue share of 65.3% in 2025, driven by the need to secure complex IT infrastructures, multi-cloud environments, and large user bases across global offices. Large organizations invest heavily in zero trust solutions to manage identity, access, and threat detection at scale while ensuring regulatory compliance.
The SME segment is expected to witness the fastest CAGR of 20.4% from 2026 to 2033, due to rising cybersecurity awareness, increasing availability of affordable and simplified zero trust platforms, and the growing reliance on cloud applications and remote workforce setups.
- By Vertical
On the basis of vertical, the Global Security Policy Management Zero Trust Security Market is segmented into Banking, Financial Services and Insurance (BFSI), IT & Telecom, Government & Defense, Energy & Utilities, Healthcare, Retail & E-commerce, and others. The BFSI vertical dominated the market with a revenue share of 28.6% in 2025, driven by stringent regulatory requirements, high-value digital assets, and the critical need to prevent data breaches and financial fraud. BFSI organizations adopt zero trust architectures to protect sensitive financial transactions and customer information while enabling secure remote access.
The IT & Telecom vertical is expected to witness the fastest CAGR of 21.2% from 2026 to 2033, fueled by rapid digital transformation, increased cloud adoption, and the need for robust identity and access management across distributed networks, data centers, and cloud applications.
Global Security Policy Management Zero Trust Security Market Regional Analysis
- North America dominated the Global Security Policy Management Zero Trust Security Market with the largest revenue share of 33% in 2025, driven by the increasing adoption of cloud services, remote work solutions, and advanced cybersecurity frameworks across enterprises and government organizations.
- Organizations in the region prioritize robust security measures, compliance with stringent data protection regulations, and the ability to manage user access and network security seamlessly across distributed environments. Zero Trust Security solutions offer these capabilities through continuous monitoring, adaptive authentication, and centralized policy enforcement.
- This widespread adoption is further supported by high IT spending, early technology adoption, and a strong presence of key solution providers. The growing demand for proactive threat detection, secure remote access, and comprehensive identity and access management has established Zero Trust Security as the preferred cybersecurity framework for enterprises, critical infrastructure, and government institutions across North America.
U.S. Zero Trust Security Market Insight
The U.S. Zero Trust Security market captured the largest revenue share of 81% in North America in 2025, driven by rapid adoption of cloud services, remote work solutions, and digital transformation initiatives. Enterprises are increasingly prioritizing proactive threat mitigation, identity management, and secure access to sensitive data. The growing demand for AI-powered analytics, adaptive authentication, and integrated policy enforcement tools is further fueling market expansion. Additionally, regulatory compliance requirements, such as CCPA and HIPAA, are compelling organizations to adopt comprehensive zero trust frameworks to protect critical IT assets and customer information.
Europe Zero Trust Security Market Insight
The Europe Zero Trust Security market is projected to expand at a substantial CAGR throughout the forecast period, primarily due to stringent data protection regulations like GDPR and the rising need for secure enterprise infrastructures. Increasing digital transformation initiatives in both public and private sectors, coupled with growing cyber threats, are driving the adoption of zero trust solutions. Organizations across financial services, government, and industrial verticals are implementing zero trust architectures to secure cloud, on-premises, and hybrid environments.
U.K. Zero Trust Security Market Insight
The U.K. Zero Trust Security market is anticipated to grow at a noteworthy CAGR during the forecast period, driven by the increasing adoption of cloud computing, remote work infrastructure, and the growing focus on cybersecurity. Concerns over ransomware, phishing attacks, and data breaches are prompting enterprises and government institutions to implement zero trust frameworks. Additionally, the U.K.’s robust IT and telecom infrastructure, coupled with strong cybersecurity awareness, is further supporting market growth.
Germany Zero Trust Security Market Insight
The Germany Zero Trust Security market is expected to expand at a considerable CAGR during the forecast period, fueled by digital transformation initiatives in enterprises and government institutions. Germany’s emphasis on data privacy, regulatory compliance, and technologically advanced IT infrastructure is promoting adoption. Organizations are increasingly deploying zero trust solutions to protect cloud applications, critical infrastructure, and enterprise networks while ensuring secure, centralized access management and continuous monitoring.
Asia-Pacific Zero Trust Security Market Insight
The Asia-Pacific Zero Trust Security market is poised to grow at the fastest CAGR of 24% from 2026 to 2033, driven by rapid digitalization, cloud adoption, and increasing cybersecurity investments in countries such as China, Japan, and India. The region’s expanding enterprise IT infrastructure, growing awareness of cyber threats, and government initiatives promoting secure digital ecosystems are propelling adoption. Additionally, the rise of large-scale IT outsourcing and distributed workforces is encouraging organizations to implement zero trust frameworks for enhanced security and operational efficiency.
Japan Zero Trust Security Market Insight
The Japan Zero Trust Security market is gaining momentum due to the country’s advanced IT infrastructure, high adoption of cloud services, and emphasis on data privacy. Enterprises are increasingly deploying zero trust architectures to manage access to sensitive information, protect cloud applications, and monitor endpoints. The growing integration of AI-based security tools and automated threat detection solutions is further boosting market growth, particularly in finance, IT, and manufacturing sectors.
China Zero Trust Security Market Insight
The China Zero Trust Security market accounted for the largest revenue share in Asia-Pacific in 2025, attributed to rapid enterprise digital transformation, cloud adoption, and strong government emphasis on cybersecurity. Large-scale organizations and state-owned enterprises are implementing zero trust frameworks to protect sensitive data, comply with cybersecurity regulations, and secure hybrid IT environments. Additionally, the presence of leading domestic cybersecurity solution providers and increasing awareness of cyber threats are key factors driving the market in China.
Global Security Policy Management Zero Trust Security Market Share
The Security Policy Management Zero Trust Security industry is primarily led by well-established companies, including:
• Cisco Systems (U.S.)
• Palo Alto Networks (U.S.)
• Microsoft (U.S.)
• Okta (U.S.)
• IBM Security (U.S.)
• Zscaler (U.S.)
• Fortinet (U.S.)
• CrowdStrike (U.S.)
• VMware (U.S.)
• Check Point Software Technologies (Israel)
• CyberArk (Israel)
• Thales Group (France)
• Trend Micro (Japan)
• Sophos (U.K.)
• Forcepoint (U.S.)
• SentinelOne (U.S.)
• RSA Security (U.S.)
• Akamai Technologies (U.S.)
• McAfee (U.S.)
• Google Cloud Security (U.S.)
What are the Recent Developments in Global Security Policy Management Zero Trust Security Market?
- In April 2024, Cisco Systems launched a strategic initiative in South Africa to strengthen enterprise cybersecurity through its advanced Zero Trust Security solutions. The initiative focuses on securing critical IT infrastructure, cloud environments, and remote workforce access for both public and private organizations. By leveraging its global expertise and AI-driven security tools, Cisco is addressing regional cybersecurity challenges while reinforcing its position in the rapidly expanding global Zero Trust Security market.
- In March 2024, Palo Alto Networks introduced the Next-Generation Zero Trust Platform 2.0, specifically designed for educational institutions and commercial enterprises. The platform enhances network and endpoint security through continuous monitoring, adaptive authentication, and automated threat response. This advancement highlights Palo Alto Networks’ commitment to providing cutting-edge cybersecurity technologies that protect sensitive data and ensure business continuity.
- In March 2024, Microsoft successfully deployed the Tokyo Secure Cloud Initiative, aimed at strengthening cloud security and access management for urban enterprises. Utilizing its AI-powered Zero Trust framework, the project enhances secure access to corporate applications and critical infrastructure, highlighting Microsoft’s focus on innovative solutions that support safer, more resilient digital ecosystems.
- In February 2024, Okta, Inc. announced a strategic partnership with Asia-Pacific financial institutions to implement a unified Zero Trust identity and access management (IAM) solution across multiple organizations. This collaboration is designed to streamline secure access, ensure regulatory compliance, and improve operational efficiency for enterprise clients, underscoring Okta’s dedication to advancing identity-driven security in complex IT environments.
- In January 2024, IBM Security unveiled the IBM Zero Trust Analytics Suite at the RSA Conference 2024. The platform integrates AI-driven threat intelligence, adaptive authentication, and real-time policy enforcement to enhance enterprise cybersecurity. IBM’s solution emphasizes convenience, scalability, and robust protection, reflecting the company’s commitment to equipping organizations with advanced tools to safeguard sensitive data across cloud, on-premises, and hybrid environments.
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
Research Methodology
Data collection and base year analysis are done using data collection modules with large sample sizes. The stage includes obtaining market information or related data through various sources and strategies. It includes examining and planning all the data acquired from the past in advance. It likewise envelops the examination of information inconsistencies seen across different information sources. The market data is analysed and estimated using market statistical and coherent models. Also, market share analysis and key trend analysis are the major success factors in the market report. To know more, please request an analyst call or drop down your inquiry.
The key research methodology used by DBMR research team is data triangulation which involves data mining, analysis of the impact of data variables on the market and primary (industry expert) validation. Data models include Vendor Positioning Grid, Market Time Line Analysis, Market Overview and Guide, Company Positioning Grid, Patent Analysis, Pricing Analysis, Company Market Share Analysis, Standards of Measurement, Global versus Regional and Vendor Share Analysis. To know more about the research methodology, drop in an inquiry to speak to our industry experts.
Customization Available
Data Bridge Market Research is a leader in advanced formative research. We take pride in servicing our existing and new customers with data and analysis that match and suits their goal. The report can be customized to include price trend analysis of target brands understanding the market for additional countries (ask for the list of countries), clinical trial results data, literature review, refurbished market and product base analysis. Market analysis of target competitors can be analyzed from technology-based analysis to market portfolio strategies. We can add as many competitors that you require data about in the format and data style you are looking for. Our team of analysts can also provide you data in crude raw excel files pivot tables (Fact book) or can assist you in creating presentations from the data sets available in the report.