Global Risk And Vulnerability Proactive Security Market
市场规模(十亿美元)
CAGR :
% 
 USD
5.55 Billion
USD
17.97 Billion
2025
2033
USD
5.55 Billion
USD
17.97 Billion
2025
2033
| 2026 –2033 | |
| USD 5.55 Billion | |
| USD 17.97 Billion | |
|
|
|
|
全球風險與漏洞主動安全市場細分,按組織規模(大型企業和中小企業)、最終用戶(銀行、金融服務和保險、政府和國防、零售和電子商務、IT和電信、醫療保健和生命科學、能源和公用事業、製造業及其他)劃分——行業趨勢及至2033年的預測
全球風險與漏洞主動安全市場規模及成長率為何?
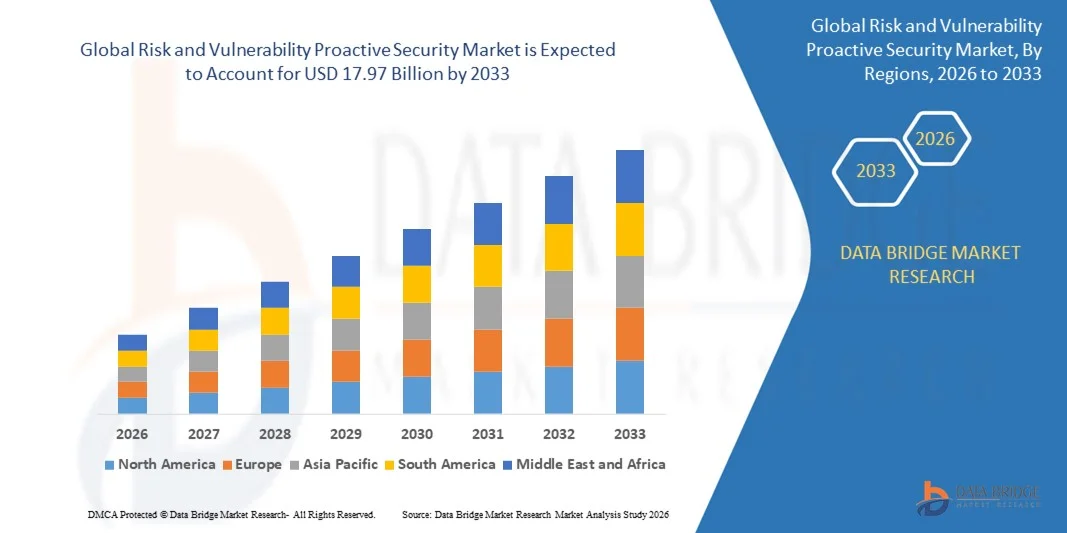
- 2025年全球風險與漏洞主動安全市場規模為55.5億美元 ,預計 2033年將達到179.7億美元,預測期內複合年增長率 為15.80%。
- 由於攻擊技術的日益複雜,戰略重心轉向主動安全,這直接影響了風險和漏洞主動安全市場的成長。
- 此外,智慧行動裝置和物聯網的日益普及也推動了風險和漏洞主動安全市場的成長。同時,日益嚴格的法規遵循要求也對該市場的成長產生了正面影響。
風險與漏洞主動安全市場的主要結論是什麼?
- 隨著安全漏洞和網路攻擊數量的增加,對主動安全解決方案的需求日益增長,這也積極推動了風險和漏洞主動安全市場的發展。
- 此外,由於自帶設備辦公室 (BYOD) 和物聯網 (IoT) 的實施,企業中互聯設備的數量不斷增長,這促使企業從被動安全解決方案轉向主動安全解決方案,從而也催生了對風險和漏洞主動安全的巨大需求,並推動了風險和漏洞主動安全市場的增長。
- 北美在風險和漏洞主動安全市場中佔據主導地位,預計到2025年將佔據39.85%的收入份額,這主要得益於美國和加拿大企業、政府機構和關鍵基礎設施營運商對網路安全的大力支持。
- 受中國、日本、印度、韓國和東南亞地區快速數位化、大規模雲端運算應用以及日益嚴峻的網路威脅的推動,亞太地區預計將在2026年至2033年間實現8.69%的最快複合年增長率。
- 大型企業細分市場預計在2025年佔據62.4%的市場份額,成為市場主導力量。這主要得益於其高額的網路安全支出、複雜的IT基礎設施以及在混合雲、多雲和全球營運環境中持續進行漏洞監控的需求。
報告範圍、風險和漏洞主動安全市場細分
|
屬性 |
風險與漏洞主動安全關鍵市場洞察 |
|
涵蓋部分 |
|
|
覆蓋國家/地區 |
北美洲
歐洲
亞太
中東和非洲
南美洲
|
|
主要市場參與者 |
|
|
市場機遇 |
|
|
加值資料資訊集 |
除了對市場狀況(如市場價值、成長率、細分、地理覆蓋範圍和主要參與者)的洞察之外,Data Bridge Market Research 精心編制的市場報告還包括深入的專家分析、定價分析、品牌份額分析、消費者調查、人口統計分析、供應鏈分析、價值鏈分析、原材料/消耗品概述、供應商選擇標準、PESTLE 分析、波特五力分析和監管框架。 |
風險與漏洞主動安全市場的主要趨勢是什麼?
人工智慧賦能、雲端驅動和自動化主動安全平台的日益融合
- 風險和漏洞主動安全市場正加速採用人工智慧驅動、雲端整合和自動化驅動的安全平台,這些平台能夠持續監控、確定優先順序並修復複雜IT環境中的網路風險。
- 供應商正在引入即時威脅分析、基於機器學習的異常偵測和自主回應功能,使組織能夠在漏洞被利用之前主動緩解漏洞。
- 企業對集中式儀錶板、自動化風險評分、持續配置監控和預測智慧的需求日益增長,正在重塑主動安全格局。
- 例如,IBM、Palo Alto Networks、思科和Rapid7等公司已經升級了其主動安全套件,增強了行為分析、自動化修復工作流程和雲端原生編排工具的功能。
- 對更快漏洞檢測、多向量威脅關聯和主動防禦機制的需求,正在推動雲端、混合和本地環境中的大規模部署。
- 隨著網路攻擊日益複雜,人工智慧驅動的主動安全平台對於全球企業的即時防護、風險預測和持續安全增強仍然至關重要。
風險和漏洞主動安全市場的主要驅動因素是什麼?
- 對進階威脅偵測、持續漏洞監控和自動化風險評估的需求不斷增長,正在推動全球企業安全生態系統對這些技術的應用。
- 例如,到2025年,IBM、思科、Securonix和LogRhythm等供應商將透過改進機器學習引擎、風險分析工具和自動化回應能力,擴展其主動安全產品組合。
- 數位轉型、雲端遷移、遠距辦公人員的增加以及網路攻擊頻率的上升,正在加速美國、歐洲和亞太地區的數位轉型和雲端遷移技術的應用。
- SIEM 整合、SOAR 自動化、端點遙測和行為分析的進步顯著提高了偵測精度、可擴展性和運作效率。
- 企業IT基礎設施日益複雜,物聯網設備、混合雲系統、SaaS平台和多向量威脅面的使用日益增多,使得主動風險識別的需求日益迫切。
- 在網路安全研發、合規需求和企業現代化等方面的持續投入推動下,風險與漏洞主動安全市場可望迎來強勁的長期成長。
哪些因素正在阻礙風險與漏洞主動安全市場的成長?
- 人工智慧驅動、以自動化為中心、雲端原生的主動安全平台部署和維護成本高昂,限制了中小企業和預算受限組織的採用。
- 例如,在2024年至2025年期間,與安全分析引擎、資料儲存和威脅情報訂閱相關的支出不斷增加,導致全球網路安全供應商的解決方案定價上漲。
- 多雲環境、加密流量分析、API 安全和零信任部署的日益複雜化,增加了對熟練網路安全專業人員的需求。
- 發展中地區對主動安全能力、自動化優勢和基於人工智慧的風險預測的認知不足,阻礙了市場滲透。
- 來自傳統 SIEM 工具、EDR 平台和手動漏洞掃描器的激烈競爭,導致價格壓力增大,並降低了高級主動式工具的差異化優勢。
- 為了克服這些障礙,供應商正著重強調成本優化的雲端產品、模組化部署、人工智慧驅動的自動化以及簡化的整合框架,以擴大主動安全解決方案在全球的應用。
風險與漏洞主動安全市場是如何細分的?
市場按組織規模和最終用戶進行細分。
- 按組織規模
根據企業規模,風險和漏洞主動安全市場可分為大型企業和中小企業 (SME)。大型企業預計將在 2025 年佔據市場主導地位,市場份額高達 62.4%,這主要得益於其高額的網路安全支出、複雜的 IT 基礎設施以及在混合雲、多雲和全球營運環境中持續進行漏洞監控的需求。大型企業越來越多地部署人工智慧驅動的風險分析、自動化威脅回應工具和持續合規平台,以應對複雜的網路攻擊和監管挑戰。其強大的投資能力、熟練的網路安全團隊以及主動防禦策略的採用,共同推動了龐大的市場需求。
受網路攻擊風險增加、雲端安全平台普及以及高性價比主動安全解決方案日益增多的推動,預計中小企業領域將在2026年至2033年間實現最快的複合年增長率。中小企業數位轉型的加速也進一步推動了自動化漏洞管理工具的採用。
- 最終用戶
根據最終用戶,風險和漏洞主動安全市場可細分為銀行、金融服務和保險 (BFSI)、政府和國防、零售和電子商務、IT 和電信、醫療保健和生命科學、能源和公用事業、製造業以及其他行業。 BFSI 產業預計將在 2025 年佔據市場主導地位,市佔率達 27.8%,這主要得益於其嚴格的監管合規要求、高交易量以及為防止資料外洩和金融詐欺而需要持續進行風險監控。 BFSI 機構高度依賴人工智慧 (AI) 賦能的風險評分、即時異常檢測和自動化事件回應系統來保護數位資產。
受雲端運算快速擴張、針對數位基礎設施的網路威脅日益增多以及應用安全、網路監控和API保護等主動安全工具的日益普及等因素推動,IT和電信行業預計將在2026年至2033年間實現最快的複合年增長率。數據流量、物聯網整合和數位服務的顯著成長進一步鞏固了長期需求。
哪個地區在風險和漏洞主動安全市場中佔最大份額?
- 北美在風險和漏洞主動安全市場中佔據主導地位,預計到2025年將佔據39.85%的收入份額,這主要得益於美國和加拿大企業、政府機構和關鍵基礎設施營運商對網路安全的大力支持。
- 網路攻擊頻率的不斷增加、進階持續性威脅 (APT) 的興起以及雲端和混合 IT 生態系統的擴展,持續加速著即時漏洞監控和主動威脅偵測解決方案的部署。
- 該地區領先企業正在整合人工智慧驅動的分析、自動化事件回應和雲端原生安全工具,從而鞏固北美在網路安全創新領域的領先地位。對數位轉型、零信任架構和先進安全營運中心 (SOC) 的持續投資進一步強化了其市場主導地位。
美國風險與漏洞主動安全市場洞察
美國仍然是北美最大的網路安全市場貢獻者,這主要得益於其高額的網路安全支出、嚴格的監管框架以及銀行、金融服務和保險 (BFSI)、國防、醫療保健和電信等行業廣泛採用主動安全工具。勒索軟體、網路釣魚和雲端攻擊帶來的風險日益增加,正在加速人工智慧增強型漏洞評估平台和自動化修復工具的部署。領先的網路安全廠商、先進的安全營運中心 (SOC) 基礎設施以及企業高度數位化水準的提升,進一步推動了市場成長。
加拿大風險與脆弱性主動安全市場洞察
加拿大為區域經濟成長做出了巨大貢獻,各組織紛紛採用主動安全系統來保護關鍵基礎設施、智慧製造環境和公共部門網路。公用事業、電信、銀行和交通運輸產業的數位化程度不斷提高,也增加了對自動化風險評分、持續監控和威脅情報工具的需求。政府主導的網路安全計畫、不斷擴大的技術創新中心以及日益增強的網路安全意識,都推動了加拿大越來越多地採用先進的主動安全解決方案。
亞太地區風險與漏洞主動安全市場
亞太地區預計在2026年至2033年間以8.69%的複合年增長率實現最快增長,這主要得益於中國、日本、印度、韓國和東南亞地區快速的數位化進程、大規模的雲端運算應用以及日益嚴峻的網路威脅。電子商務、金融服務、資料中心和5G部署的不斷擴展,推動了對高精度漏洞掃描、自動修補程式和人工智慧威脅預測工具的需求。此外,對網路安全基礎設施投資的增加、政府監管的加強以及企業對安全風險意識的提高,都將進一步加速該地區主動安全平台的普及。
中國風險與漏洞主動安全市場洞察
中國憑藉對網路安全基礎設施的大力投入、大規模的數位轉型舉措以及金融、電信和工業領域的快速發展,在亞太市場佔據領先地位。日益增長的網路攻擊風險和不斷複雜的數位生態系統正在推動漏洞評估平台、風險評分系統和人工智慧驅動的威脅管理解決方案的大規模部署。
日本風險與脆弱性主動安全市場洞察
日本在先進的工業自動化、成熟的電信基礎設施和現代化的企業網路安全框架的支撐下,保持穩定的成長。物聯網、機器人和數位化製造的日益普及,提高了對精準、即時漏洞檢測和主動風險管理工具的需求。對可靠性和長期安全規劃的高度重視,進一步推動了市場擴張。
印度風險與漏洞主動安全市場洞察
由於IT服務不斷擴張、金融科技普及以及政府支持的數位基礎設施項目,印度正迅速崛起為快速成長的市場。日益增多的網路攻擊、雲端遷移的興起以及新創企業的蓬勃發展,正在加速對持續漏洞監控、自動化合規工具和雲端原生安全平台的需求。資料中心的成長和企業數位轉型進一步推動了這些工具的普及。
韓國風險與漏洞主動安全市場洞察
韓國憑藉高技術普及率、5G的廣泛應用以及數位服務的快速發展,對全球經濟做出了顯著貢獻。對互聯設備、人工智慧系統和工業自動化的日益依賴,也提升了對先進漏洞管理和即時威脅情報解決方案的需求。強大的製造業能力和創新驅動的數位生態系統,為韓國的長期穩定成長提供了支撐。
風險與漏洞主動安全市場中的領導企業有哪些?
風險和漏洞主動安全產業主要由一些知名企業引領,其中包括:
- IBM公司(美國)
- FireEye公司(美國)
- Palo Alto Networks, Inc.(美國)
- Securonix公司(美國)
- LogRhythm公司(美國)
- Rapid7(美國)
- Qualys公司(美國)
- AT&T智慧財產權。 (美國)
- 麥克菲有限責任公司(美國)
- Trustwave Holdings, Inc.(美國)
- CyberSponse公司(美國)
- 思科(美國)
- 博通公司(美國)
- FireMon, LLC(美國)
- Centrify公司(美國)
- 甲骨文(美國)
- 泳道(美國)
- Skybox Security, Inc.(美國)
- RSA Security LLC(美國)
- ThreatConnect公司(美國)
SKU-
Get online access to the report on the World's First Market Intelligence Cloud
- Interactive Data Analysis Dashboard
- Company Analysis Dashboard for high growth potential opportunities
- Research Analyst Access for customization & queries
- Competitor Analysis with Interactive dashboard
- Latest News, Updates & Trend analysis
- Harness the Power of Benchmark Analysis for Comprehensive Competitor Tracking
研究方法
数据收集和基准年分析是使用具有大样本量的数据收集模块完成的。该阶段包括通过各种来源和策略获取市场信息或相关数据。它包括提前检查和规划从过去获得的所有数据。它同样包括检查不同信息源中出现的信息不一致。使用市场统计和连贯模型分析和估计市场数据。此外,市场份额分析和关键趋势分析是市场报告中的主要成功因素。要了解更多信息,请请求分析师致电或下拉您的询问。
DBMR 研究团队使用的关键研究方法是数据三角测量,其中包括数据挖掘、数据变量对市场影响的分析和主要(行业专家)验证。数据模型包括供应商定位网格、市场时间线分析、市场概览和指南、公司定位网格、专利分析、定价分析、公司市场份额分析、测量标准、全球与区域和供应商份额分析。要了解有关研究方法的更多信息,请向我们的行业专家咨询。
可定制
Data Bridge Market Research 是高级形成性研究领域的领导者。我们为向现有和新客户提供符合其目标的数据和分析而感到自豪。报告可定制,包括目标品牌的价格趋势分析、了解其他国家的市场(索取国家列表)、临床试验结果数据、文献综述、翻新市场和产品基础分析。目标竞争对手的市场分析可以从基于技术的分析到市场组合策略进行分析。我们可以按照您所需的格式和数据样式添加您需要的任意数量的竞争对手数据。我们的分析师团队还可以为您提供原始 Excel 文件数据透视表(事实手册)中的数据,或者可以帮助您根据报告中的数据集创建演示文稿。