1 INTRODUCTION
1.1 OBJECTIVES OF THE STUDY
1.2 MARKET DEFINITION
1.3 OVERVIEW OF GLOBAL FILELESS ATTACK SECURITY MARKET
1.4 CURRENCY AND PRICING
1.5 LIMITATION
1.6 MARKETS COVERED
2 MARKET SEGMENTATION
2.1 KEY TAKEAWAYS
2.2 ARRIVING AT THE GLOBAL FILELESS ATTACK SECURITY MARKET
2.3 VENDOR POSITIONING GRID
2.4 TECHNOLOGY LIFE LINE CURVE
2.5 MARKET GUIDE
2.6 MULTIVARIATE MODELLING
2.7 TOP TO BOTTOM ANALYSIS
2.8 STANDARDS OF MEASUREMENT
2.9 VENDOR SHARE ANALYSIS
2.1 DATA POINTS FROM KEY PRIMARY INTERVIEWS
2.11 DATA POINTS FROM KEY SECONDARY DATABASES
2.12 GLOBAL FILELESS ATTACK SECURITY MARKET: RESEARCH SNAPSHOT
2.13 ASSUMPTIONS
3 MARKET OVERVIEW
3.1 DRIVERS
3.2 RESTRAINTS
3.3 OPPORTUNITIES
3.4 CHALLENGES
4 EXECUTIVE SUMMARY
5 PREMIUM INSIGHTS
5.1 VALUE CHAIN ANALYSIS
5.2 BRAND ANALYSIS
5.3 ECOSYSTEM MARKET MAP
5.4 TECHNOLOGICAL TRENDS
5.5 TOP WINNING STRATEGIES
5.6 PORTER’S FIVE FORCES ANALYSIS
6 GLOBAL FILELESS ATTACK SECURITY MARKET, BY TYPE
6.1 OVERVIEW
6.2 MACROS
6.3 IN MEMORY
6.4 SCRIPTS
6.5 OTHERS
7 GLOBAL FILELESS ATTACK SECURITY MARKET, BY SECURITY TECHNOLOGIES
7.1 OVERVIEW
7.2 ENDPOINT SECURITY
7.2.1 MULTILAYERED SECURITY ENGINES
7.2.2 SYSTEM HARDENING
7.2.3 DECEPTION
7.3 ENDPOINT DETECTION & RESPONSE (EDR)
7.4 EMAIL SECURITY
7.5 NETWORK SECURITY
7.6 OTHERS
8 GLOBAL FILELESS ATTACK SECURITY MARKET, BY ATTACK TECHNOLOGY
8.1 OVERVIEW
8.2 MEMORY-ONLY THREATS
8.3 DUAL-USE TOOLS
8.4 FILELESS PERSISTENCE METHODS
8.5 NON-PORTABLE EXECUTABLE (PE) FILE ATTACKS
8.6 OTHERS
9 GLOBAL FILELESS ATTACK SECURITY MARKET, BY APPLICATION
9.1 OVERVIEW
9.2 AEROSPACE & DEFENSE
9.2.1 BY TYPE
9.2.1.1. MACROS
9.2.1.2. IN MEMORY
9.2.1.3. SCRIPTS
9.2.1.4. OTHERS
9.3 BFSI
9.3.1 BY TYPE
9.3.1.1. MACROS
9.3.1.2. IN MEMORY
9.3.1.3. SCRIPTS
9.3.1.4. OTHERS
9.4 GOVERNMENT
9.4.1 BY TYPE
9.4.1.1. MACROS
9.4.1.2. IN MEMORY
9.4.1.3. SCRIPTS
9.4.1.4. OTHERS
9.5 IT & TELECOM
9.5.1 BY TYPE
9.5.1.1. MACROS
9.5.1.2. IN MEMORY
9.5.1.3. SCRIPTS
9.5.1.4. OTHERS
9.6 HEALTHCARE
9.6.1 BY TYPE
9.6.1.1. MACROS
9.6.1.2. IN MEMORY
9.6.1.3. SCRIPTS
9.6.1.4. OTHERS
9.7 RETAIL
9.7.1 BY TYPE
9.7.1.1. MACROS
9.7.1.2. IN MEMORY
9.7.1.3. SCRIPTS
9.7.1.4. OTHERS
9.8 E-COMMERCE
9.8.1 BY TYPE
9.8.1.1. MACROS
9.8.1.2. IN MEMORY
9.8.1.3. SCRIPTS
9.8.1.4. OTHERS
9.9 EDUCATION
9.9.1 BY TYPE
9.9.1.1. MACROS
9.9.1.2. IN MEMORY
9.9.1.3. SCRIPTS
9.9.1.4. OTHERS
9.1 OTHERS
9.10.1 BY TYPE
9.10.1.1. MACROS
9.10.1.2. IN MEMORY
9.10.1.3. SCRIPTS
9.10.1.4. OTHERS
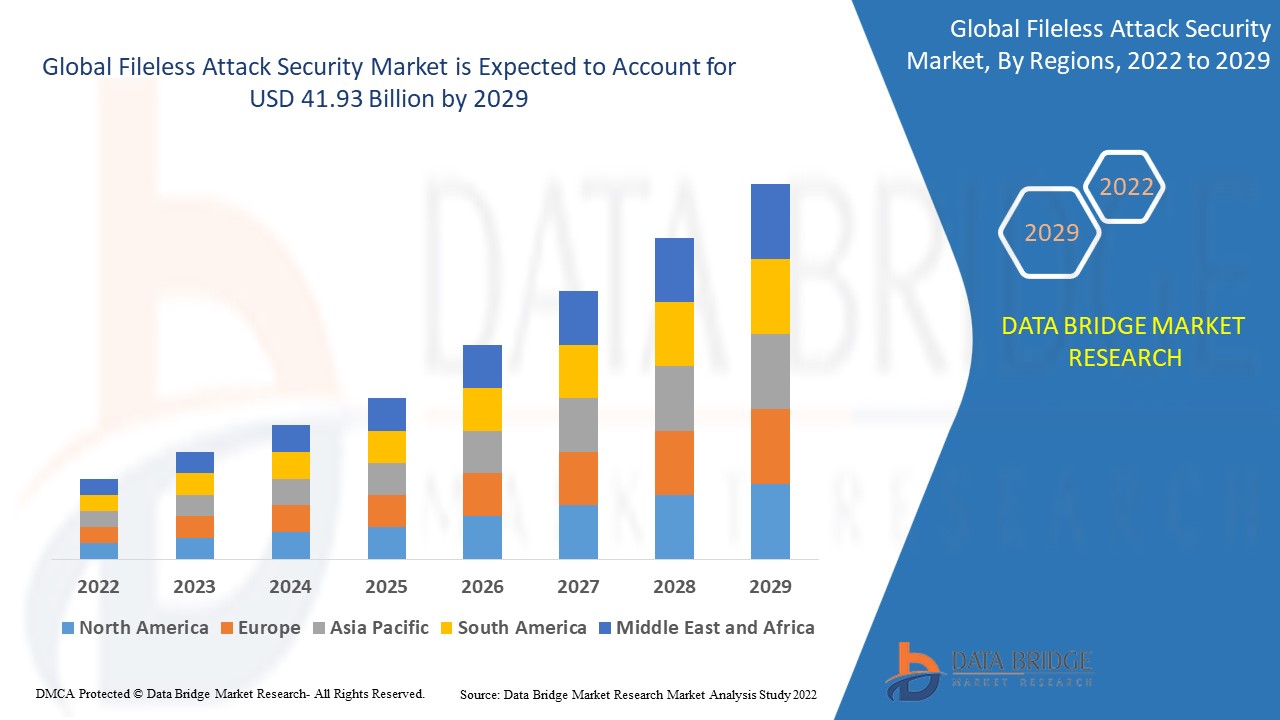
10 GLOBAL FILELESS ATTACK SECURITY MARKET, BY REGION
Global FILELESS ATTACK SECURITY Market, (ALL SEGMENTATION PROVIDED ABOVE IS REPRESENTED IN THIS CHAPTER BY COUNTRY)
10.1 NORTH AMERICA
10.1.1 U.S.
10.1.2 CANADA
10.1.3 MEXICO
10.2 EUROPE
10.2.1 GERMANY
10.2.2 FRANCE
10.2.3 U.K.
10.2.4 ITALY
10.2.5 SPAIN
10.2.6 RUSSIA
10.2.7 TURKEY
10.2.8 BELGIUM
10.2.9 NETHERLANDS
10.2.10 SWITZERLAND
10.2.11 DENMARK
10.2.12 SWEDEN
10.2.13 POLAND
10.2.14 NORWAY
10.2.15 FINLAND
10.2.16 REST OF EUROPE
10.3 ASIA PACIFIC
10.3.1 JAPAN
10.3.2 CHINA
10.3.3 SOUTH KOREA
10.3.4 INDIA
10.3.5 AUSTRALIA
10.3.6 SINGAPORE
10.3.7 THAILAND
10.3.8 MALAYSIA
10.3.9 INDONESIA
10.3.10 PHILIPPINES
10.3.11 NEW ZEALAND
10.3.12 TAIWAN
10.3.13 VIETNAM
10.3.14 REST OF ASIA PACIFIC
10.4 SOUTH AMERICA
10.4.1 BRAZIL
10.4.2 ARGENTINA
10.4.3 REST OF SOUTH AMERICA
10.5 MIDDLE EAST AND AFRICA
10.5.1 SOUTH AFRICA
10.5.2 EGYPT
10.5.3 BAHRAIN
10.5.4 QATAR
10.5.5 KUWAIT
10.5.6 OMAN
10.5.7 SAUDI ARABIA
10.5.8 U.A.E
10.5.9 ISRAEL
10.5.10 REST OF MIDDLE EAST AND AFRICA
10.6 KEY PRIMARY INSIGHTS: BY MAJOR COUNTRIES
11 GLOBAL FILELESS ATTACK SECURITY MARKET, COMPANY LANDSCAPE
11.1 COMPANY SHARE ANALYSIS: NORTH AMERICA
11.2 COMPANY SHARE ANALYSIS: EUROPE
11.3 COMPANY SHARE ANALYSIS: ASIA-PACIFIC
11.4 MERGERS & ACQUISITIONS
11.5 NEW PRODUCT DEVELOPMENT & APPROVALS
11.6 EXPANSIONS
11.7 REGULATORY CHANGES
11.8 PARTNERSHIP AND OTHER STRATEGIC DEVELOPMENTS
12 GLOBAL FILELESS ATTACK SECURITY MARKET, SWOT ANALYSIS
13 GLOBAL FILELESS ATTACK SECURITY MARKET, COMPANY PROFILE
13.1 AMAZON WEB SERVICES
13.1.1 COMPANY SNAPSHOT
13.1.2 REVENUE ANALYSIS
13.1.3 GEOGRAPHIC PRESENCE
13.1.4 PRODUCT PORTFOLIO
13.1.5 RECENT DEVELOPMENTS
13.2 TATA CONSULTANCY SERVICES
13.2.1 COMPANY SNAPSHOT
13.2.2 REVENUE ANALYSIS
13.2.3 GEOGRAPHIC PRESENCE
13.2.4 PRODUCT PORTFOLIO
13.2.5 RECENT DEVELOPMENTS
13.3 MICROSOFT
13.3.1 COMPANY SNAPSHOT
13.3.2 REVENUE ANALYSIS
13.3.3 GEOGRAPHIC PRESENCE
13.3.4 PRODUCT PORTFOLIO
13.3.5 RECENT DEVELOPMENTS
13.4 MICRO FOCUS
13.4.1 COMPANY SNAPSHOT
13.4.2 REVENUE ANALYSIS
13.4.3 GEOGRAPHIC PRESENCE
13.4.4 PRODUCT PORTFOLIO
13.4.5 RECENT DEVELOPMENTS
13.5 F-SECURE
13.5.1 COMPANY SNAPSHOT
13.5.2 REVENUE ANALYSIS
13.5.3 GEOGRAPHIC PRESENCE
13.5.4 PRODUCT PORTFOLIO
13.5.5 RECENT DEVELOPMENTS
13.6 MCAFEE
13.6.1 COMPANY SNAPSHOT
13.6.2 REVENUE ANALYSIS
13.6.3 GEOGRAPHIC PRESENCE
13.6.4 PRODUCT PORTFOLIO
13.6.5 RECENT DEVELOPMENTS
13.7 FORTINET, INC
13.7.1 COMPANY SNAPSHOT
13.7.2 REVENUE ANALYSIS
13.7.3 GEOGRAPHIC PRESENCE
13.7.4 PRODUCT PORTFOLIO
13.7.5 RECENT DEVELOPMENTS
13.8 FORCEPOINT
13.8.1 COMPANY SNAPSHOT
13.8.2 REVENUE ANALYSIS
13.8.3 GEOGRAPHIC PRESENCE
13.8.4 PRODUCT PORTFOLIO
13.8.5 RECENT DEVELOPMENTS
13.9 RAPID7
13.9.1 COMPANY SNAPSHOT
13.9.2 REVENUE ANALYSIS
13.9.3 GEOGRAPHIC PRESENCE
13.9.4 PRODUCT PORTFOLIO
13.9.5 RECENT DEVELOPMENTS
13.1 FIREYE, INC
13.10.1 COMPANY SNAPSHOT
13.10.2 REVENUE ANALYSIS
13.10.3 GEOGRAPHIC PRESENCE
13.10.4 PRODUCT PORTFOLIO
13.10.5 RECENT DEVELOPMENTS
13.11 CHECKPOINT SOFTWARE TECHNOLOGIES, LTD
13.11.1 COMPANY SNAPSHOT
13.11.2 REVENUE ANALYSIS
13.11.3 GEOGRAPHIC PRESENCE
13.11.4 PRODUCT PORTFOLIO
13.11.5 RECENT DEVELOPMENTS
13.12 IMPERVA
13.12.1 COMPANY SNAPSHOT
13.12.2 REVENUE ANALYSIS
13.12.3 GEOGRAPHIC PRESENCE
13.12.4 PRODUCT PORTFOLIO
13.12.5 RECENT DEVELOPMENTS
13.13 KASPERSKY LAB
13.13.1 COMPANY SNAPSHOT
13.13.2 REVENUE ANALYSIS
13.13.3 GEOGRAPHIC PRESENCE
13.13.4 PRODUCT PORTFOLIO
13.13.5 RECENT DEVELOPMENTS
13.14 BREWER SCIENCE, INC
13.14.1 COMPANY SNAPSHOT
13.14.2 REVENUE ANALYSIS
13.14.3 GEOGRAPHIC PRESENCE
13.14.4 PRODUCT PORTFOLIO
13.14.5 RECENT DEVELOPMENTS
13.15 INTERLINK ELECTRONICS, INC
13.15.1 COMPANY SNAPSHOT
13.15.2 REVENUE ANALYSIS
13.15.3 GEOGRAPHIC PRESENCE
13.15.4 PRODUCT PORTFOLIO
13.15.5 RECENT DEVELOPMENTS
13.16 MURATA MANUFACTURING CO, LTD
13.16.1 COMPANY SNAPSHOT
13.16.2 REVENUE ANALYSIS
13.16.3 GEOGRAPHIC PRESENCE
13.16.4 PRODUCT PORTFOLIO
13.16.5 RECENT DEVELOPMENTS
13.17 HONEYWELL
13.17.1 COMPANY SNAPSHOT
13.17.2 REVENUE ANALYSIS
13.17.3 GEOGRAPHIC PRESENCE
13.17.4 PRODUCT PORTFOLIO
13.17.5 RECENT DEVELOPMENTS
13.18 TE CONNECTIVITY
13.18.1 COMPANY SNAPSHOT
13.18.2 REVENUE ANALYSIS
13.18.3 GEOGRAPHIC PRESENCE
13.18.4 PRODUCT PORTFOLIO
13.18.5 RECENT DEVELOPMENTS
13.19 THIN FILM ELECTRONICS
13.19.1 COMPANY SNAPSHOT
13.19.2 REVENUE ANALYSIS
13.19.3 GEOGRAPHIC PRESENCE
13.19.4 PRODUCT PORTFOLIO
13.19.5 RECENT DEVELOPMENTS
13.2 MTS SYSTEMS CORPORATION
13.20.1 COMPANY SNAPSHOT
13.20.2 REVENUE ANALYSIS
13.20.3 GEOGRAPHIC PRESENCE
13.20.4 PRODUCT PORTFOLIO
13.20.5 RECENT DEVELOPMENTS
13.21 DIGI-KEY ELECTRONICS
13.21.1 COMPANY SNAPSHOT
13.21.2 REVENUE ANALYSIS
13.21.3 GEOGRAPHIC PRESENCE
13.21.4 PRODUCT PORTFOLIO
13.21.5 RECENT DEVELOPMENTS
13.22 DUPONT
13.22.1 COMPANY SNAPSHOT
13.22.2 REVENUE ANALYSIS
13.22.3 GEOGRAPHIC PRESENCE
13.22.4 PRODUCT PORTFOLIO
13.22.5 RECENT DEVELOPMENTS
13.23 ISORG
13.23.1 COMPANY SNAPSHOT
13.23.2 REVENUE ANALYSIS
13.23.3 GEOGRAPHIC PRESENCE
13.23.4 PRODUCT PORTFOLIO
13.23.5 RECENT DEVELOPMENTS
13.24 QUALYS, INC
13.24.1 COMPANY SNAPSHOT
13.24.2 REVENUE ANALYSIS
13.24.3 GEOGRAPHIC PRESENCE
13.24.4 PRODUCT PORTFOLIO
13.24.5 RECENT DEVELOPMENTS
NOTE: THE COMPANIES PROFILED IS NOT EXHAUSTIVE LIST AND IS AS PER OUR PREVIOUS CLIENT REQUIREMENT. WE PROFILE MORE THAN 100 COMPANIES IN OUR STUDY AND HENCE THE LIST OF COMPANIES CAN BE MODIFIED OR REPLACED ON REQUEST
14 RELATED REPORTS
15 QUESTIONNAIRE
16 ABOUT DATA BRIDGE MARKET RESEARCH